
Here, we explain how data leaks happen and how you can stop them. We gave you detailed instructions on how to set up security protocols.
First, let's talk about what it means. When sensitive, private, or protected data is copied, sent, viewed, stolen, or used by someone who isn't supposed to, this is called a data breach. It's pretty clear what this is about, but let's look at who and how.
There are many different causes of personal information leakage. These are the main ones:
- because employees or developers were careless and left databases, ports, and other things open;
- employees who lose data on purpose;
- Security holes on the website.
To make things easier to understand, let's divide the different types of data leaks into two groups: those that are done on purpose and those that are not.
Most of the time, data leaks happen by accident in the medical services industry. Employees are responsible for up to 60% of leaks in the healthcare industry, but only 20% were intentional. Employee negligence was to blame for the other 80%.
A lot of data leaks happen by accident in the education, housing, and community services sectors as well. In general, though, 72% of data leaks happen on purpose around the world. Most of the time, attacks happen against banks, insurance companies, and government agencies.
Where can I find information, and what could it lead me to?
It's a safe bet that when personal information gets out, fraudsters do more of it. You should be very careful if someone calls you from a number you don't know and says they are from your bank. It's probably a scam.
In a strange way, these leaks are often used for marketing purposes as well. You can make a profile of a person if you do some research and combine data from different services. Discover his favorite foods, places to visit, and shows to watch. With this kind of portrait, you can feel someone's pain and know where to "press."
The same data that was leaked can be found on the dark web, which is why it's used in all hacker movies. It's a shame, but the dark web has everything.
How can you keep yourself safe?
There's no doubt that security is the most important thing. It applies to websites, mobile apps, computers, and phones. A complete step is to keep hackers from getting into your server. Here is a short but very important list of things you can do to keep hackers out:
- Logging in with an SSH key.
- Good old VPN
- Use TLS or SSL
- Authentication with two factors
Logging in with an SSH key.
As an alternative to a password, you could use an SSH key. It has two parts, one that is public and one that is private. It is longer than a password.
The open one goes in the home directory of the user who is connecting to the server, and the closed one goes in the home directory of the user who is connecting to the remote server. This means that these two parts are "compared," and if everything is fine, they are let in.
How to make a key for SSH
OS Windows lets you connect to remote servers via SSH. One example of this is the Putty client. It doesn't need to be installed; all you have to do to use it is unpack the archive you downloaded.
Run puttygen.exe once the files have been unpacked. Choose the 2048-bit length and SSH-2 RSA key type, then click the Generate button:
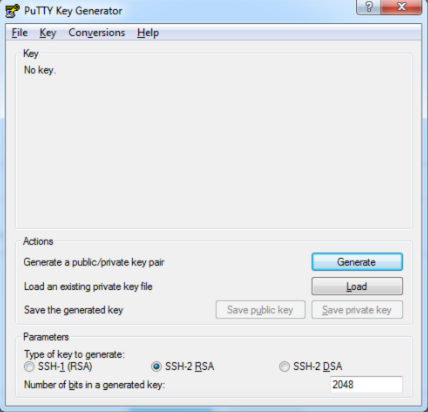
Move the cursor over an empty part of the window during generation. This is needed to make pseudo-randomness. Use the "Save public key" and "Save private key" buttons to save the key pair on your computer. Copy the key that was made and paste it where it says to:

VPN
As a user, you can make a safe connection to a network made up of several computers using virtual private network technology. It's also used to get around restrictions and keep your privacy safe online.
SSL and TLS
It is possible to set up and use a cryptographically secure connection between a client and a server over the Internet with TLS. It gives clients a way to verify servers. It's used by servers to make sure that clients are real (when this is important).
2FA - Two-Factor Authentication
Two types of verification are used for this type of authentication. For the most part, this is a login name and password plus a code. This kind of access makes things very hard for attackers, but it's not a foolproof way to keep people safe.



Comments 0