
Fraudsters do not want the money of ordinary hard workers, they have set their sights on insurance companies.
Ransomware malware called HardBit has been updated to version 2.0. Now the perpetrators are trying to negotiate with the victims to pay a ransom that their insurance company can cover.
According to a report from security and data analytics company Varonis, the first version of HardBit was spotted in October 2022. A month later, in November 2022, version 2.0 came into play. It is she who remains the most common version of HardBit at the moment.
Unlike most other ransomware, HardBit does not have a site where the leaked data will be uploaded after the timer expires. However, the ransomware themselves, in their note, claim that the encrypted data has been stolen and threaten to leak it if the ransom is not paid.
HardBit 2.0 has some features to reduce security on the victim's system. For example, malware can modify the Windows registry to affect the built-in Microsoft Defender, rendering it ineffective. The malware also enters Windows startup and deletes all archived backups created by the system so that the user cannot restore their data.
An interesting feature of the malware is the data encryption stage itself. Instead of writing encrypted data to copies of files and deleting the originals, as many ransomware do, HardBit 2.0 works on the original files by overwriting their contents with encrypted data. This approach greatly complicates the recovery of the original files and slightly speeds up encryption.
The HardBit 2.0 memo does not specify the specific amount of money that the hackers want to receive in exchange for the decryption key. Victims are given 48 hours to contact the attacker via a secure peer-to-peer messaging application.
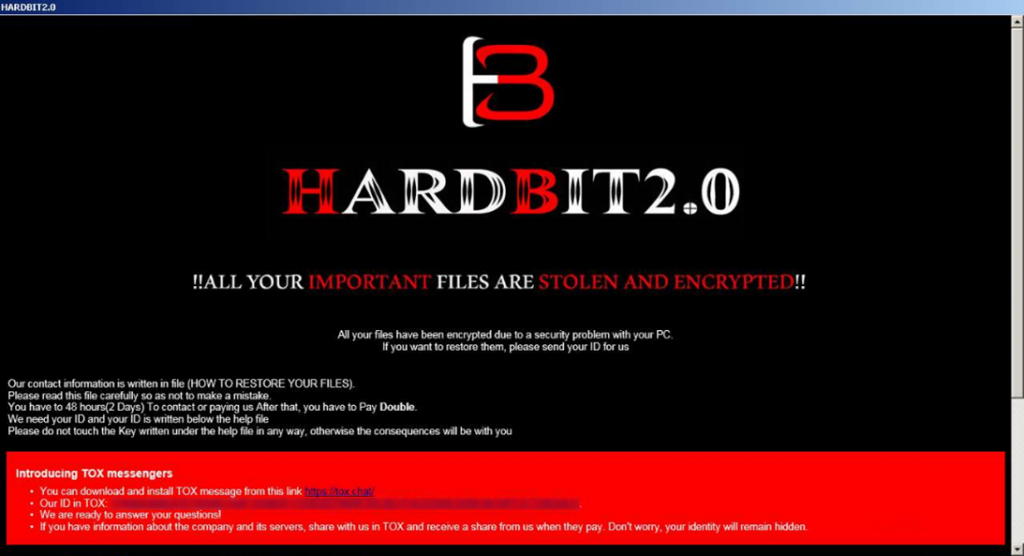
For those victims who have insurance against cyberattacks, hackers have a more detailed set of instructions and encourage them to disclose the sum insured for a successful dialogue. Moreover, cyber-thugs cast insurance companies in the worst possible light, assuring that insurers never negotiate with extortionists and do not take into account the interests of their clients.
“To avoid all this and get the insurance money, be sure to tell us about the terms of the insurance coverage. This benefits both you and us, but not the insurance company,” HardBit operators say in a note to victims. The hackers claim that they will adjust the ransom amount so that the victims of the attack do not pay anything out of their own pocket.
According to the insurance contract, it is impossible to disclose the details of insurance to malefactors, this can lead to the loss of any chance that the insurer will cover the losses. That's why HardBit insists that this data be shared anonymously.
However, regardless of the extortionists' assurances, their goal is to get money. Fraudsters can promise anything, but you should not trust them. Refusing to pay the ransom and reporting the incident to law enforcement are the only surefire ways to deal with this type of threat.


Comments 0