
The dark web, a part of the internet that is not indexed by search engines and requires specific software for access, has been a topic of considerable interest and concern due to its association with illegal activities. While the dark web can serve as a platform for privacy-protected activities and a refuge for those under oppressive regimes, it has also been the scene of numerous notorious cases.
1. The Silk Road

The Silk Road was an online black market and the first modern darknet market, best known as a platform for selling illegal drugs. Launched in February 2011 by Ross Ulbricht, it operated as a Tor hidden service, allowing users to browse it anonymously and securely without potential traffic monitoring. The name "Silk Road" was chosen to evoke the historical trade routes connecting the East and West, suggesting a digital era of commerce, albeit in illicit goods.
Silk Road utilized a sophisticated encryption system to enable users to make purchases anonymously, using Bitcoin as its primary form of payment to further obscure the identities of buyers and sellers. The marketplace became known for selling a variety of illegal drugs but also offered other illicit goods and services. Its inventory expanded to include fake documents, stolen data, and services such as hacking. The site was designed with a user-friendly interface, resembling mainstream e-commerce websites, which contributed to its popularity and widespread use.
The anonymity provided by the dark web and the use of cryptocurrency made Silk Road an emblem of the digital age's libertarian ideals, challenging traditional law enforcement methods and raising debates on privacy, digital rights, and the war on drugs. However, this anonymity also made it a target for law enforcement agencies worldwide. The FBI shut down Silk Road in October 2013 and arrested Ross Ulbricht, known by his pseudonym "Dread Pirate Roberts". Ulbricht was convicted of money laundering, computer hacking, conspiracy to traffic fraudulent identity documents, and conspiracy to traffic narcotics.
The closure of Silk Road did not end the trade of illegal goods on the dark web; instead, it led to the emergence of new marketplaces like Agora and Silk Road 2.0. These platforms sought to replicate the original's success by offering similar illicit products and services, employing advanced security measures to protect their operations and users' anonymity. Despite the efforts of law enforcement, which led to the shutdown of Silk Road 2.0 and the voluntary closure of Agora due to security concerns, the cycle of new marketplaces appearing continues. This phenomenon underscores the persistent demand for such anonymous trading environments and highlights the challenges authorities face in curbing illegal online activities.
2. Edward Snowden

The case of Edward Snowden remains one of the most pivotal and divisive events in the modern discourse on digital privacy, government surveillance, and the ethical boundaries of national security. In 2013, Snowden, a former NSA contractor and CIA employee, made the unprecedented decision to leak thousands of classified documents, shedding light on the vast and previously undisclosed extent of the United States' and its allies' global surveillance programs. This revelation sparked intense debates across the world on the rights to privacy, the limits of governmental power, and the definition of whistleblowing versus treason.
Born on June 21, 1983, in Elizabeth City, North Carolina, Snowden's trajectory took him from a high school dropout to a position where he had access to some of the most sensitive information held by the United States government. Despite lacking a formal university education, Snowden's aptitude for information technology propelled him through the ranks of the intelligence community, eventually leading to roles that exposed him to classified surveillance programs.
In a bold move, Snowden left his job in 2013, citing the need for epilepsy treatment as a cover, and flew to Hong Kong. There, he met with journalists Glenn Greenwald, Laura Poitras, and Ewen MacAskill, to whom he disclosed the documents. The contents revealed, among other things, the PRISM program, which allowed the NSA access to data from major tech companies, and the bulk collection of telephone metadata from millions of Americans without their consent. These revelations not only shocked the public but also ignited a global conversation on the necessity and ethics of mass surveillance in the name of national security.
The fallout from Snowden's disclosures was immediate and far-reaching. He was celebrated by many as a hero and whistleblower for bringing these practices to light, while others condemned him as a traitor who compromised national security. The debate extended into legal and legislative arenas, influencing significant reforms like the USA Freedom Act of 2015, which aimed to curtail some of the NSA's surveillance activities.
Following the leaks, Snowden found himself a man without a country, stranded in Moscow's Sheremetyevo International Airport after the U.S. revoked his passport. Russia eventually granted him asylum, a status he maintains to this day, living in a state of exile. Despite being charged by the U.S. government under the Espionage Act, Snowden continues to be a vocal advocate for privacy rights and governmental transparency.
3. Julian Assange

Julian Assange is a figure known worldwide for his role in founding WikiLeaks, a platform that publishes classified and leaked documents with the aim of promoting transparency and accountability. Born on July 3, 1971, in Townsville, Australia, Assange's early life was marked by frequent moves and an unconventional education, which played a role in shaping his skeptical outlook on government and authority.
In 2006, Assange launched WikiLeaks, which came to international prominence in 2010 with the release of a series of leaks provided by U.S. Army intelligence analyst Chelsea Manning. These leaks included the "Collateral Murder" video, which showed U.S. soldiers killing 18 people in Baghdad, Iraq, in July 2007; the Afghanistan and Iraq War logs, which detailed military operations and incidents; and Cablegate, a release of more than 250,000 U.S. diplomatic cables.
Assange's work with WikiLeaks has polarized public opinion. Supporters view him as a champion of free speech and transparency, who has taken considerable personal risks to expose government secrets, corruption, and abuses of power. Critics, however, argue that his releases have endangered lives, compromised national security, and irresponsibly exposed sensitive information.
Legal troubles have significantly impacted Assange's life. In 2010, he faced sexual assault allegations in Sweden, which he claimed were politically motivated and intended to extradite him to the United States, where he feared facing charges related to WikiLeaks' activities. Assange sought asylum in the Embassy of Ecuador in London in 2012 to avoid extradition to Sweden, resulting in a seven-year stay until his asylum was revoked in 2019. Following this, he was arrested by British police and has been fighting extradition to the U.S., where he faces 18 charges, including conspiracy to commit computer intrusion.
The debate surrounding Assange is not just about the individual but encompasses broader themes of media freedom, the right to information, and the ethical boundaries of journalism and whistleblowing. His case raises critical questions about the balance between national security and transparency, the role of journalists in holding governments accountable, and the legal and moral implications of leaking classified information.
4. Child exploitation networks

Child exploitation networks consist of forums, websites, and peer-to-peer networks that specialize in the creation, distribution, and consumption of child sexual abuse materials (CSAM). These platforms often employ strict access controls, including invitation-only memberships, payment in cryptocurrencies, and the use of encryption technologies to maintain secrecy and protect the identities of their users. The content shared within these networks is not only illegal but also profoundly harmful to the victims of child sexual abuse, perpetuating their victimization and trauma.
The anonymity features of the dark web that protect user privacy also create significant barriers for law enforcement agencies attempting to infiltrate and dismantle child exploitation networks. However, international collaboration and advances in digital forensics have led to several high-profile successes. Operations such as Operation Delego and Operation Blackwrist have resulted in the identification and arrest of individuals involved in these networks and the rescue of numerous victims.
In these operations, law enforcement agencies have employed a variety of tactics, including undercover operations, hacking, and the use of court-approved network investigative techniques (NITs) to bypass anonymity protections.
5. Evite data breach

In 2019, Evite, a popular online invitation and social planning service, faced a significant security challenge when it experienced a massive data breach. This breach compromised the personal information and IP addresses of more than 10 million users.
The breach occurred in April when an unauthorized party, later identified as the hacker known as Gnosticplayers, gained access to Evite's servers. This intrusion allowed the attacker to exfiltrate a substantial volume of user data, including names, email addresses, passwords, and, in some cases, dates of birth and phone numbers. Notably, Evite clarified that financial information, such as credit card details, was stored separately and remained unaffected by the breach.
Gnosticplayers, rather than immediately releasing the stolen data to the public, contacted Evite with a ransom demand: $1900 in Bitcoin. This amount is relatively minor compared to the potential costs and damages associated with data breaches of this magnitude, which can escalate to millions of dollars in settlements and reparatory actions. Evite chose not to pay the ransom, leading Gnosticplayers to start selling the stolen information on the dark web during the summer of 2019. Fortunately, the marketplace where this information was being sold was shut down shortly thereafter.
Evite's response to the breach included public acknowledgment and a detailed outline of the steps the company was taking to address the situation. These steps included conducting a thorough security audit and enhancing their security measures to prevent future breaches. Additionally, Evite urged affected users to reset their passwords as a precautionary measure.
6. Death Grips' 'No Love Deep Web'

In the lead-up to the release of "No Love Deep Web", the experimental hip-hop group Death Grips orchestrated a unique promotional campaign that captivated the curiosity of their audience. In August 2012, they launched an alternate reality game (ARG) on the dark web, inviting participants into a complex puzzle that blurred the lines between the digital world and physical reality.
This game was reminiscent of the infamous Cicada 3301 puzzles, known for their intricate design and the use of various encryption methods. Death Grips' ARG utilized a plethora of cryptographic techniques, including the Caesar cipher, QR codes, and Morse code, among others. Clues were meticulously hidden across various sites on the dark web, creating a treasure hunt that required participants to employ a broad range of skills to decipher messages and follow the trail laid out by the band.
The objective of this elaborate game wasn't recruitment for a secretive organization or a cybercriminal plot; it was a promotional strategy for "No Love Deep Web". By engaging their audience in this manner, Death Grips not only generated buzz around their upcoming album but also provided an immersive experience that mirrored the album's themes of paranoia, technology, and subversion. This approach to promotion was unconventional, leveraging the mystique of the dark web to foster a sense of intrigue and exclusivity around the album's release.
7. Peter Scully case

The case of Peter Scully is one of the most disturbing instances of child exploitation in the digital age, highlighting the darkest aspects of the internet and the global challenge of combating online child abuse. An Australian national, Scully moved to the Philippines in 2011, where he committed horrific crimes that shocked law enforcement agencies and the public worldwide.
Once in the Philippines, Scully engaged in the production and distribution of child pornography involving the torture and abuse of young children. His crimes were not only brutal but also meticulously documented and sold on the dark web. Among his most infamous productions was a video series titled "Daisy's Destruction", which depicted the appalling abuse of children. This content, sold to international pedophiles, became one of the most notorious cases of child exploitation material ever circulated on the dark web.
Scully's activities eventually caught the attention of Philippine authorities and international law enforcement agencies, leading to his arrest in February 2015. The investigation revealed a horrifying pattern of abuse, manipulation, and exploitation, with Scully and his accomplices luring impoverished children with promises of food or money. Following his arrest, Scully faced multiple charges, including human trafficking, rape, and murder.
In response to the atrocities committed by Scully and the broader issue of online child exploitation, there have been calls for stricter regulations on internet content, enhanced monitoring tools, and greater resources for digital forensics. The case has also led to increased public awareness and education on the dangers of the dark web and the importance of safeguarding children online.
8. Operation Dark HunTor

Operation Dark HunTor was a significant international law enforcement operation aimed at targeting illegal activities on the dark web, particularly focusing on the sale of drugs, weapons, and other illicit goods and services.
Operation Dark HunTor was the result of collaborative efforts involving agencies from several countries, including the FBI, Europol, and law enforcement from countries such as Germany, the Netherlands, and the UK, among others. This operation was part of a larger crackdown on illegal online marketplaces, following the takedowns of other notorious sites like the DeepSea and Berlusconi.
The primary objective of Operation Dark HunTor was to disrupt the ecosystem of illegal dark web marketplaces and bring to justice those responsible for running and using such platforms. The operation led to the arrest of hundreds of individuals across the globe and the seizure of millions of dollars in cash and cryptocurrencies, drugs, weapons, and other illegal goods.
Operation Dark HunTor marked a pivotal moment in the ongoing battle against dark web criminal enterprises. It highlighted the importance and effectiveness of international cooperation in addressing cybercrime. The operation also served as a warning to both operators and users of illegal dark web marketplaces, showing that anonymity on the internet is not infallible and that law enforcement agencies are continuously evolving their methods to combat digital crime.
9. Operation DisrupTor
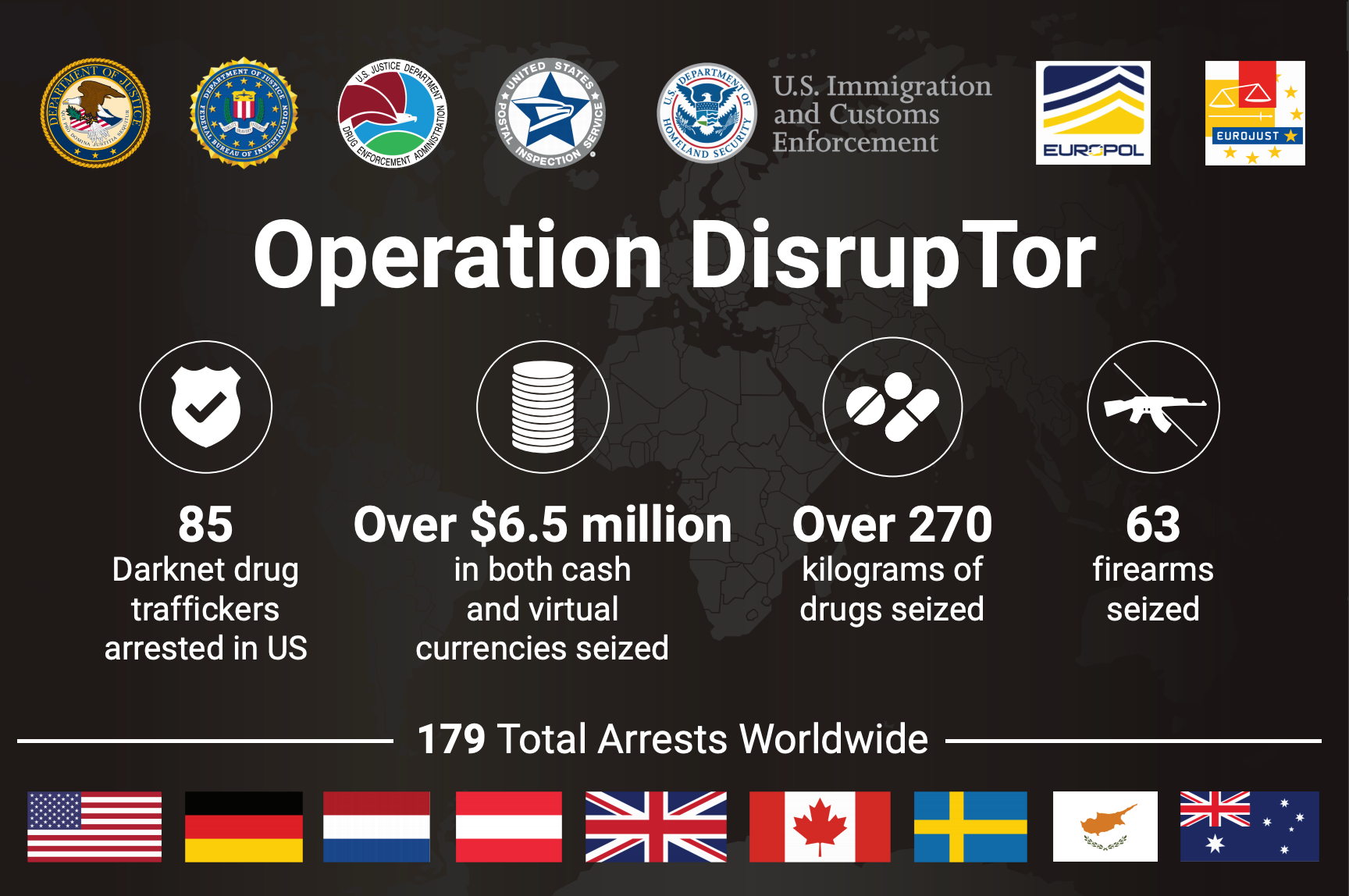
Operation DisrupTor is a landmark international law enforcement initiative aimed at dismantling the networks behind the sale of drugs, weapons, and other illicit goods on the dark web.
The operation was the result of extensive coordination between agencies from Europe and the United States, including Europol, the FBI, and the DEA, among others. Operation DisrupTor showcased the power of collaborative intelligence-sharing and operational planning across borders to target and dismantle criminal networks operating online.
The impact of Operation DisrupTor was significant, resulting in the arrest of hundreds of suspects across the world. The operation also led to the seizure of substantial quantities of drugs, firearms, and millions of dollars in cash and cryptocurrencies. By targeting vendors and buyers on various dark web marketplaces, the operation disrupted the supply chains of illegal goods and services, demonstrating the vulnerabilities of even the most secretive online criminal enterprises.
A key to the operation's success was the use of advanced cyber investigative techniques and technologies to trace the physical-world identities of dark web users. Law enforcement agencies exploited the digital breadcrumbs left by transactions and communications on the dark web, despite the layers of anonymity provided by encryption and Tor. This painstaking detective work was augmented by leveraging information from previous operations and infiltrating criminal communities online.
10. Hiring Hitmen on the Dark Web

The concept of hiring a hitman through the dark web has emerged as a chilling example of how the anonymity provided by this part of the internet can be exploited for nefarious purposes. While the vast majority of transactions and interactions on the dark web are benign, the notion that it could be used to commission crimes has drawn significant attention from law enforcement, researchers, and the public.
Websites allegedly offering hitman services have appeared, claiming to facilitate the hiring of individuals to commit assaults or murders for financial compensation.
Law enforcement agencies worldwide have taken the threat of dark web hitman services seriously, resulting in several sting operations and arrests. These investigations often reveal that many sites purporting to offer such services are scams, designed to extort money from individuals willing to pay for the commission of a crime. However, the mere existence of these sites and the intent shown by some individuals to use them represent a disturbing use of digital anonymity for criminal purposes.
In response, agencies have developed sophisticated cyber investigative techniques to trace the activities of individuals attempting to hire hitmen on the dark web. These techniques include the deployment of undercover agents, the analysis of bitcoin transactions, and the use of digital forensics to unmask users' true identities.
Conclusion
The exploration of the dark web through various cases offers a comprehensive look into the complexities and challenges of policing the digital underworld. These instances highlight the persistent battle between the innovative use of technology for criminal purposes and the equally sophisticated efforts of law enforcement to uphold justice and protect vulnerable populations.
The narrative surrounding the dark web is a stark reminder of the internet's dual nature—as a tool for both empowerment and exploitation. The anonymity and freedom it affords, while being pillars of privacy and free speech, can also serve as a shield for those committing dangerous acts.





Comments 0