
The tools and technologies designed to streamline and secure internet usage can sometimes be twisted for malicious intent. One such tool is the reverse proxy, commonly deployed by businesses to enhance their online services. While reverse proxies are essential in optimizing and securing internet traffic, they can also be exploited by cybercriminals to execute sophisticated scams.
- What is a Reverse Proxy?
- Benefits of using a Reverse Proxy
- The malicious use of Reverse Proxies
- Countermeasures and prevention strategies
- Conclusion
What is a Reverse Proxy?
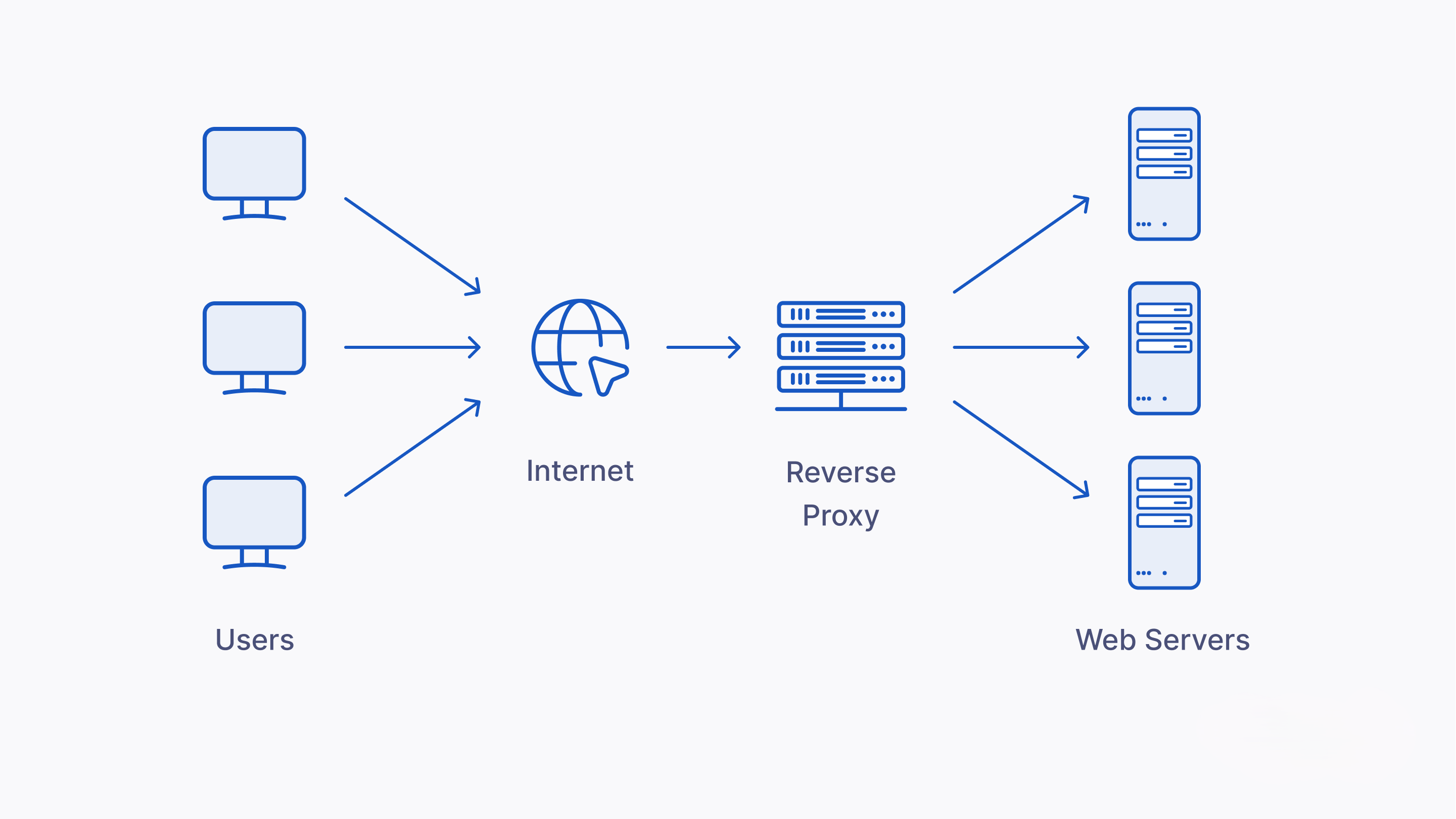
A reverse proxy is a type of server that sits between a user's browser and a web server. It intercepts requests from users before they reach the server. This is in contrast to a forward proxy, which is used by clients to access multiple servers. Reverse proxies are installed in the network of the server and are designed to be transparent to the end user.
Key functions of reverse proxies:
- Load balancing. One of the primary functions of a reverse proxy is load balancing, which distributes incoming traffic across multiple servers. This distribution helps to optimize resources, reduce individual server load, and improve website response times, making websites more resilient to spikes in traffic and less prone to downtime.
- Web acceleration. Reverse proxies can cache content and compress incoming and outgoing data, significantly speeding up web access for users. By storing static content (like images and HTML pages) and serving it directly from the proxy server, it reduces the load on the origin server and delivers content faster.
- Security and anonymity. Enhancing security is another crucial role of reverse proxies. They can obscure the true backend server's IP address, protecting it from direct external attacks. Furthermore, reverse proxies can perform SSL encryption, ensuring that data transferred between the client and the server is secure and encrypted, thus safeguarding sensitive information from interceptors.
- Application firewall features. Implementing application-level firewall capabilities, reverse proxies can scrutinize incoming traffic to filter out harmful requests before they reach the server. This includes blocking attacks such as SQL injection, cross-site scripting (XSS), and cross-site forgery (CSRF), among others.
Benefits of using a Reverse Proxy
- Improved server security. By acting as a shield, reverse proxies protect backend servers from exposure to direct internet traffic. This setup minimizes the risk of attack vectors that can exploit vulnerabilities in server configurations.
- Enhanced performance. Through caching and load balancing, reverse proxies enhance the performance of web applications. They reduce the time it takes to serve content to end-users, improving the overall user experience.
- Simplified SSL management. Managing SSL/TLS certificates on a reverse proxy rather than on individual servers simplifies the encryption of traffic, centralizing and streamlining security management.
- Flexibility and scalability. Reverse proxies facilitate more straightforward infrastructure scaling and maintenance without impacting the end user’s experience or modifying the backend servers.
The malicious use of Reverse Proxies

Cybercriminals can use reverse proxies to intercept and manipulate data, impersonate legitimate services, and ultimately scam users. Here are some ways in which these systems can be exploited:
Interception of sensitive data
One of the primary malicious uses of reverse proxies involves intercepting sensitive data transmitted between the user and legitimate services. Cybercriminals can configure reverse proxies to act as a man-in-the-middle, capturing and potentially altering data without the knowledge of either the user or the service provider. This data often includes login credentials, financial information, and personal details, which can be used for fraud or identity theft.
Impersonation and phishing attacks
Attackers use reverse proxies to create convincing replicas of legitimate websites. Users are redirected to these fraudulent proxies through phishing emails or compromised websites. Once there, any information entered, such as passwords or credit card numbers, is sent directly to the attackers. This method is particularly effective because the proxy can make the malicious site appear more legitimate and secure, even displaying valid SSL certificates.
Session hijacking and credential theft
By routing user sessions through a malicious reverse proxy, attackers can effectively hijack user sessions. This allows them to steal session cookies and other tokens, gaining unauthorized access to user accounts. This type of attack can be particularly damaging on e-commerce sites, banking platforms, and other online services where users remain logged in for extended periods.
Countermeasures and prevention strategies

To combat the risks posed by the malicious use of reverse proxies, both individuals and organizations can adopt several effective strategies.
Enhanced awareness and vigilance
Education plays a critical role in preventing proxy-based attacks. Users should be aware of the signs of phishing, such as slight URL changes or unsolicited requests for sensitive information, and be cautious with links in emails or messages, especially from unknown sources.
Robust security protocols
Organizations should implement strict security measures, including HTTPS protocols, two-factor authentication, and regular security audits to identify and mitigate vulnerabilities. Regularly updating software and systems can also prevent attackers from exploiting known vulnerabilities.
Network monitoring and anomaly detection
Advanced monitoring tools can detect unusual traffic patterns or alterations in data flow that may indicate the presence of a reverse proxy attack. By analyzing both inbound and outbound traffic, these tools can alert administrators to potential security breaches.
Legal and regulatory compliance
Adhering to industry standards and legal requirements can further protect against reverse proxy attacks. Regulations such as GDPR in Europe and various cybersecurity laws in other regions enforce standards that help safeguard user data and ensure proper security practices are followed.
Use a VPN
Virtual Private Networks (VPN) are pivotal in enhancing online privacy, especially when using public Wi-Fi networks, which are often targets for cybercriminals. A VPN encrypts your internet connection, making it more difficult for attackers to intercept or manipulate your data.
Be cautious about sharing personal data
Limit the amount of personal information you share on social media and other online platforms. Cybercriminals can exploit this data for social engineering and phishing attacks. Being mindful about what you share online can protect you from various online scams and identity theft.
Regularly update your software
Keeping software up to date is a critical aspect of cybersecurity. Regular updates often include patches for security vulnerabilities that could be exploited by hackers. By staying current with software updates, you enhance your defenses against the evolving techniques of cyber attackers.
Conclusion
While reverse proxies are a cornerstone technology in modern web infrastructure, their exploitation by cybercriminals poses significant risks. The misuse of reverse proxies in online scams highlights a significant challenge within cyber security, illustrating the complex dual nature of technology—it can protect or it can harm.
To navigate this terrain, businesses and individuals alike must remain vigilant. Implementing robust security measures, staying informed about the latest cyber threats, and fostering a culture of cybersecurity awareness are paramount. Regular audits, continuous monitoring, and adopting best practices in network security can dramatically reduce the risk posed by malicious reverse proxies.




Comments 0