
The world will soon witness fresh software-based extortion schemes.
Recently, the complete source code for the initial HelloKitty ransomware was made available on a cybercrime forum. The person who posted the data revealed the creation of a brand-new, stronger encryptor.
A cybersecurity researcher using the alias "3xp0rt" found the source code. He discovered that the hacker posting the archive containing the code for the sixth of October went by the online alias "kapuchin0," also known as "Gookee."
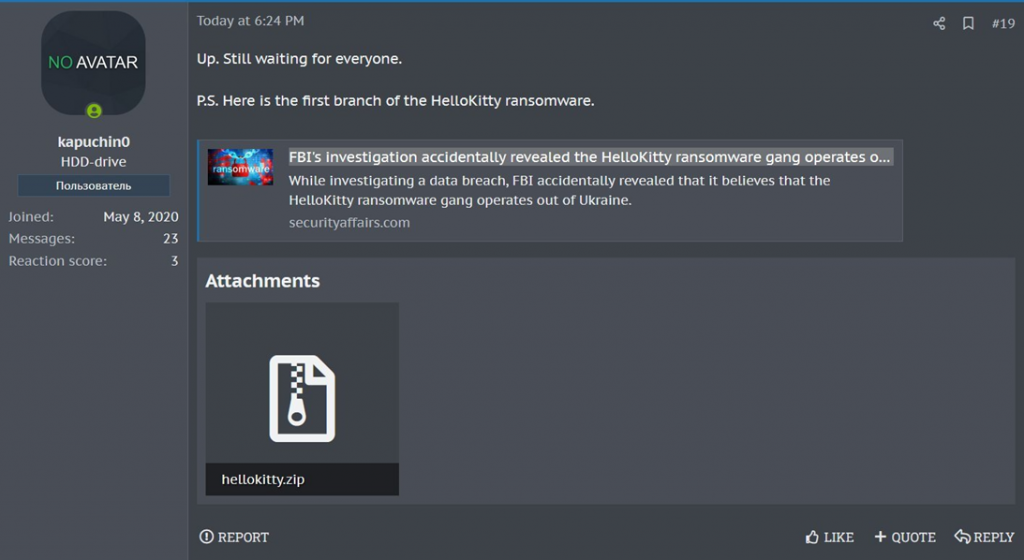
Posting by "kapuchin0" on a forum for cybercrime
Gookee has a history of being connected to dishonest behavior. It attempted to sell malware source codes, offered access to Sony Network Japan in 2020, and even offered its own RaaS service called "Gooke Ransomware."
The HelloKitty encryptor was reportedly created directly by kapuchin0/Gookee, who is also reportedly working on a new product that will, in his opinion, be much more intriguing than the buzzworthy Lockbit.
The HelloKitty encryptor and decryptor, as well as the NTRUEncrypt library used by this variant of the malware to encrypt files, are created by a ready-made Microsoft Visual Studio solution that is included in the publicly available hellokitty.zip archive.
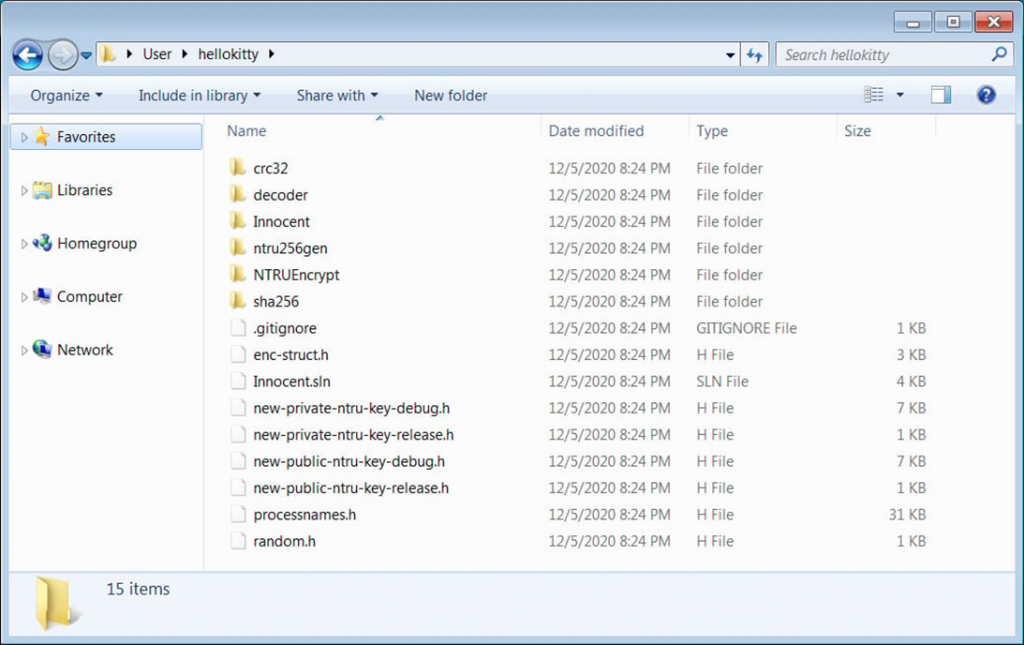
Contents of the archive as published
This is the actual HelloKitty source code that was used to launch the operation in 2020, according to ransomware expert Michael Gillespie.
Although making ransomware source code available to the public might advance security research, there are still more drawbacks than benefits. Typically, cybercriminals quickly modify open source code to suit their purposes and produce numerous forks of a specific malware to carry out their own malicious activities.
Since its inception in November 2020, Operation HelloKitty has been known for its attacks on corporate networks, data theft, and system encryption. In February 2021, the Polish company CD Projekt Red was the target of the most well-known ransomware attack, in which the attackers made a public announcement about stealing the source code of several studio games.
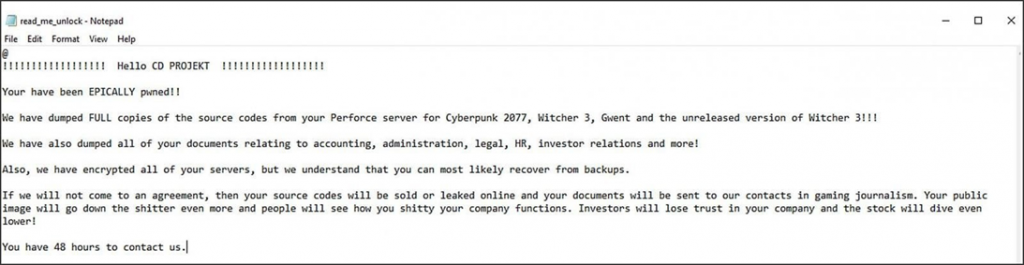
Personal message from HelloKitty hackers to CD Projekt Red
Other names, such as DeathRansom, Fivehands, and possibly Abyss Locker, have also been used to refer to the HelloKitty ransomware and its variants.
To aid cybersecurity experts in identifying HelloKitty, the Federal Bureau of Investigation (FBI) even disseminated a comprehensive list of indicators of compromise in late October 2021. However, this information may now be dated.



Comments 0