
The safeguarding of information stands as a testament to human ingenuity and the relentless pursuit of privacy. Born from a global call to fortify data security, Advanced Encryption Standard (AES) encryption weaves together the dual threads of advanced technology and collective trust, providing a secure foundation upon which the edifice of modern communication is built. Through its universal adoption, AES not only encrypts our most sensitive data but also embodies our shared commitment to safeguarding the digital realm.
AES encryption
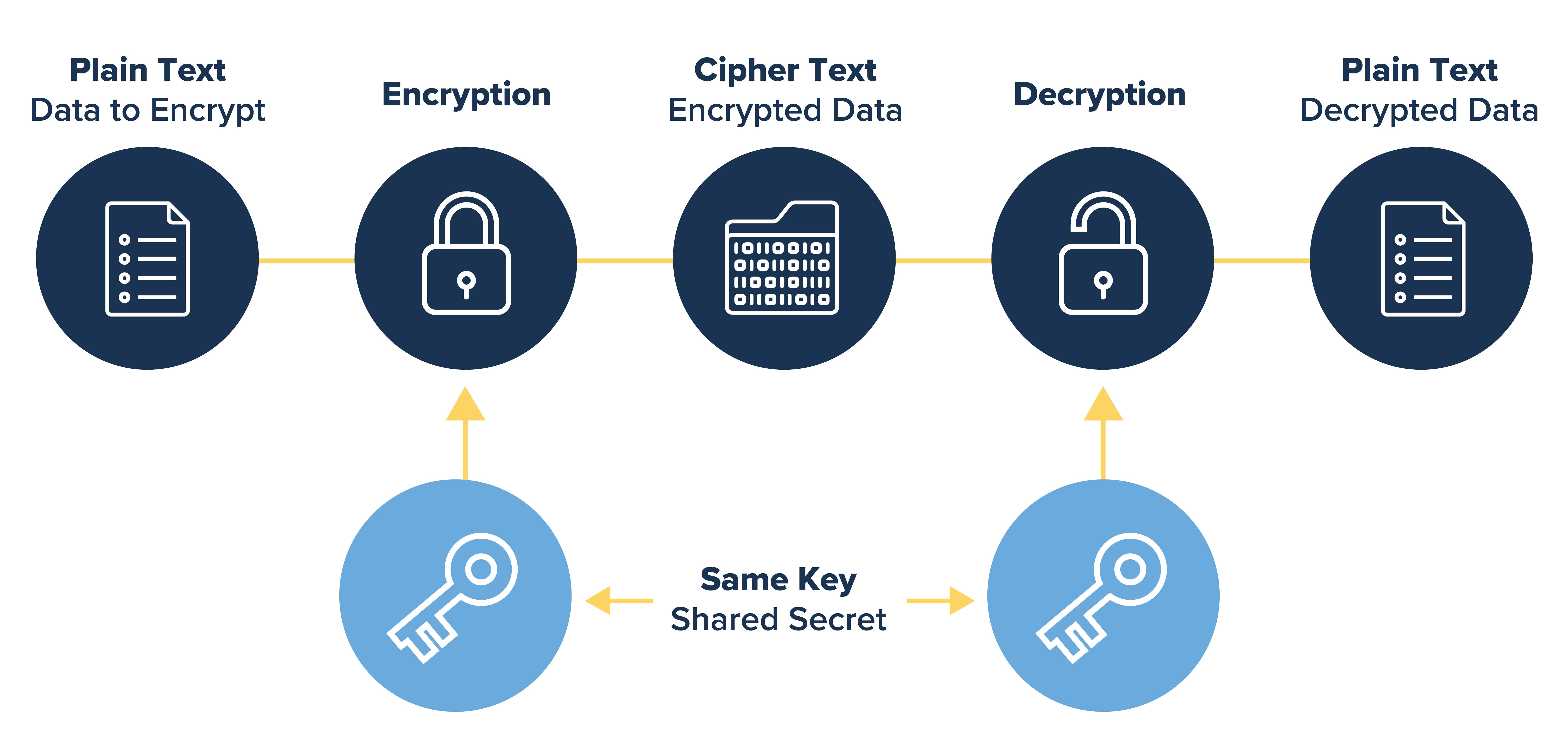
AES is a symmetric key encryption algorithm, which means it uses the same key for both encrypting and decrypting information. This characteristic simplifies key management in many scenarios, making AES both versatile and efficient for a wide array of applications. The standard operates on data blocks of 128 bits, through key sizes of 128, 192, or 256 bits, accommodating varying levels of security requirements. The choice of key size adjusts the number of transformation rounds that data undergoes during encryption, balancing between the imperatives of security and performance.
What sets AES apart is not just its robustness against cryptographic attacks, but also its adaptability across diverse platforms—from hardware to software, from tiny microcontrollers to powerful servers. This versatility ensures that AES can protect sensitive information everywhere, from the secure storage on your smartphone to confidential communications across the globe.
The evolution of AES encryption
As the 20th century waned, the digital revolution was accelerating, bringing with it an unprecedented flow of information. However, this new era also heralded emerging threats to digital security, highlighting the limitations of the existing Data Encryption Standard (DES). DES, once a bulwark of digital encryption, began to crumble under the pressure of advancing computational capabilities, prompting the search for a successor capable of withstanding the tests of time and technology.
In 1997, the U.S. National Institute of Standards and Technology (NIST) cast a global net, inviting cryptographers to develop an encryption standard that could serve as the new armament against cyber threats. This initiative was not just about finding a replacement for DES; it was a clarion call to the global cryptographic community to contribute to a foundational aspect of digital security. The response was a vibrant display of international cooperation and intellectual prowess, with submissions from around the world.
The selection process was rigorous and transparent. After exhaustive analysis and public scrutiny, the algorithm proposed by Belgian cryptographers Vincent Rijmen and Joan Daemen, known as Rijndael, emerged victorious in 2000. Its selection was not merely a testament to its technical superiority but also to its adaptability across various platforms and its performance in a wide range of applications.
In 2001, Rijndael was officially adopted as the AES, marking a new epoch in the annals of cryptography. This transition was more than a technical update; it was a reflection of the changing dynamics of global information security. AES was embraced not only by governments and financial institutions but also by the broader tech community, becoming a standard bearer for encryption in the digital age.
Where is the AES encryption used?
1. Internet security
AES is integral to securing the internet. It encrypts data transferred over the web, including emails, online transactions, and personal information. Protocols like Secure Sockets Layer (SSL) and Transport Layer Security (TLS) rely on AES to establish secure connections between web servers and browsers, ensuring that online communications remain confidential and tamper-proof.
2. Financial services
The financial sector, where security is paramount, utilizes AES to protect sensitive information such as credit card numbers, account details, and financial transactions. Banks and financial institutions deploy AES within their databases and during data transit to shield against data breaches and fraud, thereby maintaining trust and integrity in financial systems.
3. Government and military
Due to its robust security features, AES is approved by the U.S. National Security Agency (NSA) for protecting classified information. Governments and military organizations around the world employ AES to safeguard their most sensitive data, from national security documents to strategic communication.
4. Consumer electronics
In the realm of consumer electronics, AES encryption is ubiquitous. Smartphones, tablets, and personal computers use AES to encrypt user data, ensuring privacy and security. Whether it’s protecting photos, messages, or personal notes, AES forms a protective barrier against unauthorized access.
5. Wireless security
Wireless networks, including Wi-Fi, are protected using AES. Standards like WPA3 employ AES to secure wireless communications, preventing unauthorized access and ensuring that the data transmitted over wireless networks remains secure from eavesdropping and other cyber threats.
6. Cloud storage
As more data migrates to the cloud, AES encryption ensures that information stored in cloud services remains secure. Cloud providers leverage AES to encrypt data both at rest and in transit, offering a robust layer of protection against data breaches and unauthorized access.
7. Enterprise security solutions
Within enterprises, AES is used to encrypt sensitive business information, including employee records, intellectual property, and internal communications. AES enables businesses to maintain confidentiality and compliance with data protection regulations, building a secure environment for both data and operations.
8. VPN services
Virtual Private Network (VPN) services use AES to secure internet connections, allowing users to browse with anonymity and security. By encrypting the data tunnel between the user’s device and the VPN server, AES ensures that the user’s online activities are shielded from surveillance and data interception.
AES encryption process
Before the actual encryption begins, AES undertakes a preparatory step known as key expansion. The original encryption key is used to generate a series of distinct Round Keys through a process of permutations and substitutions. This ensures a unique key for each round of encryption, adding to the complexity and security of the algorithm. The key expansion phase is critical because it prepares the groundwork for the intricate series of transformations that follow.
Initial Round
The data, organized into blocks of 128 bits, enters the initial round, where it's combined with the first round key through a simple operation called AddRoundKey. This melds the data and key together, setting the stage for the rounds to follow.
Main Rounds
Each of the main rounds (nine, eleven, or thirteen rounds, depending on the key length) involves four sequential operations:
- SubBytes (Substitution Bytes). This step uses a non-linear substitution table (S-box) to replace each byte in the block with another byte according to a predefined rule. This substitution introduces complexity and helps to thwart attacks based on statistical analysis.
- ShiftRows. The rows of the block are cyclically shifted by different offsets. The first row remains unchanged, the second row is shifted one byte to the left, the third row two bytes, and the fourth row three bytes. This step disperses the bytes across the column, contributing to diffusion throughout the block.
- MixColumns. In this transformation, each column of the block is mixed using a mathematical operation. The columns are treated as polynomials over a finite field and multiplied modulo a fixed polynomial, further scrambling the data. This step ensures that the transformation of each column affects the others, enhancing the algorithm's resistance to cryptographic attacks.
- AddRoundKey (again). Similar to the initial round, the modified data block is combined with a new round key through a bitwise XOR operation. This step integrates the effects of the previous transformations with the round key, preparing the block for the next round of processing.
Final Round
The final round omits the MixColumns step, proceeding directly from the ShiftRows to the AddRoundKey operation. This slight modification concludes the encryption process, producing the encrypted data block, known as ciphertext.
Decrypting with AES
Decrypting with the Advanced Encryption Standard is essentially the mirror image of its encryption process, unwinding the complex layers of data transformation to reveal the original plaintext. This symmetric decryption process employs the same key used for encryption but navigates through the algorithm's steps in reverse order, using inverse operations to methodically dismantle the encrypted state.
Inverse operations such as Inverse ShiftRows, Inverse SubBytes, and Inverse MixColumns are applied, each step methodically undoing the effects of its encryption counterpart. Every byte is carefully restored to its original state, culminating in the revelation of the original data after the initial round key is applied for the last time.
AES security

Advanced Encryption Standard is renowned for its robust security and is currently considered one of the most secure encryption algorithms available. However, like all encryption algorithms, AES is not entirely without theoretical vulnerabilities, though it's important to note that most of these concerns are primarily of academic interest rather than practical threats. Here are some aspects related to AES security considerations:
1. Brute force attacks
AES, with its 128, 192, or 256-bit key sizes, offers a high level of security against brute force attacks, which involve trying every possible key until the correct one is found. The sheer number of possible keys in AES makes such attacks impractical with current and foreseeable computing technology. However, the theoretical possibility exists, especially as computational power continues to grow, albeit at a pace unlikely to threaten AES's effectiveness in the near to medium term.
2. Side-channel attacks
These attacks don't target the AES algorithm itself but rather aim to exploit vulnerabilities in its implementation, particularly how encryption is executed on hardware and software. By analyzing information like power consumption, timing information, electromagnetic leaks, or even sounds, attackers might gain insights into the encryption process and potentially retrieve the encryption key. Mitigating these risks requires careful attention to the specific implementation and environment in which AES is used.
3. Cryptanalytic attacks
While no effective cryptanalytic attacks have broken AES, researchers continuously test the algorithm against new attack methods. For instance, attacks like the biclique attack have been theoretically proposed against AES, but these require such a significant amount of computational resources and time that they remain impractical for undermining AES's security in any realistic scenario.
4. Future threats
Quantum computing represents a future threat to many encryption algorithms, including AES. Although a large-scale quantum computer capable of breaking AES encryption does not yet exist, its potential development could challenge current cryptographic standards. That said, AES-256 is considered to be more resilient against quantum attacks compared to AES-128, due to its longer key length.
Conclusion
Born from a meticulous selection process and refined through global collaboration, AES transcends its technical roots to become a symbol of trust and resilience in our interconnected world. Its widespread adoption across various sectors—from securing personal communications to safeguarding national security—speaks volumes about its reliability and efficiency. As we navigate the ever-expanding digital landscape, AES remains a steadfast guardian of data integrity, ensuring that our digital interactions remain private and secure.




Comments 0