
With the growing awareness of surveillance and data breaches, individuals are seeking alternative ways to communicate and browse the internet securely. One such solution that has gained attention is the Invisible Internet Project (I2P).
What is I2P?
Imagine a hidden network running parallel to the familiar internet, shielded from prying eyes and data snoopers. This clandestine realm is the realm of I2P, the Invisible Internet Project. Unlike the internet we commonly navigate, I2P operates in the shadows, prioritizing privacy and anonymity above all else.
At its core, I2P is an anonymous overlay network, designed to provide a secure haven for communication and browsing. It works by encrypting data and routing it through a decentralized network of volunteer-run nodes, obscuring the identity and location of both the sender and the recipient.
Think of I2P as a secret tunnel system, where data travels incognito, shielded by layers of encryption and bouncing through a series of intermediary nodes. This decentralized routing mechanism ensures that even if a node is compromised, the data remains indecipherable to prying eyes.
How does I2P work?
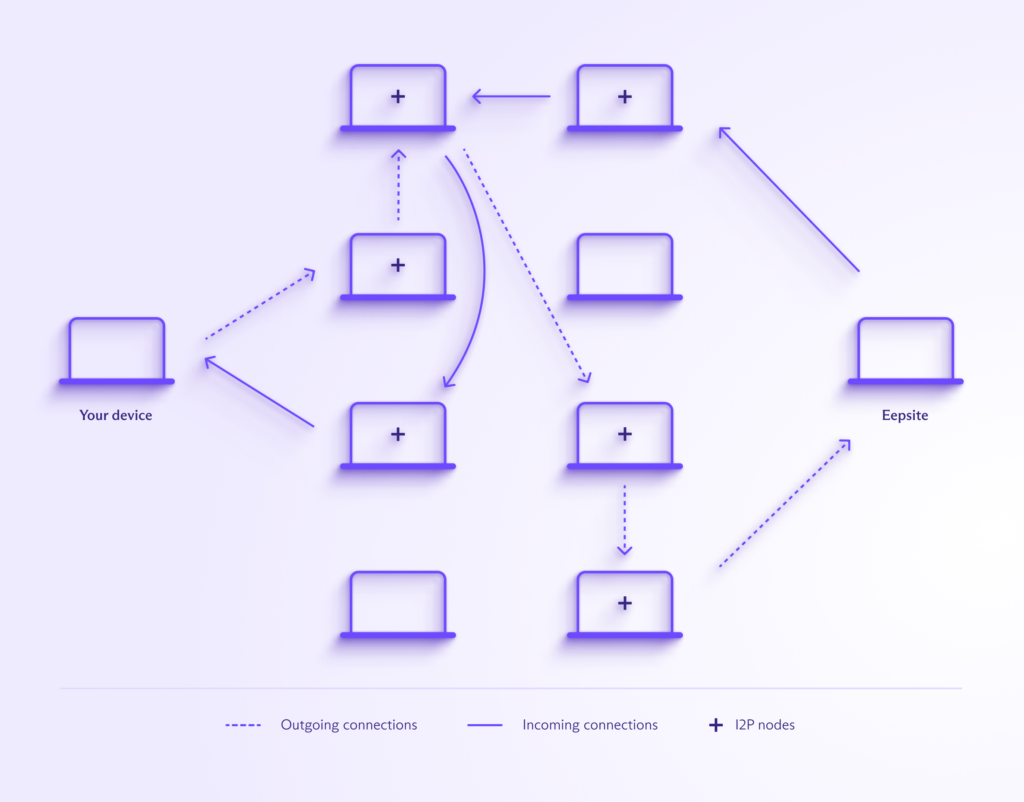
I2P operates as a decentralized peer-to-peer (P2P) network, relying on its community to maintain its functionality. When you use I2P, your traffic undergoes a process of encryption and routing through a network of volunteer-maintained nodes spread across the globe. This network comprises over 50,000 devices, ensuring that your data is dispersed globally, making it incredibly challenging for any potential spies to intercept.
Let's delve into why I2P is regarded as a highly secure network:
End-to-End encryption: Your data is encrypted from its source to its destination, with the endpoints of your data route transformed into cryptographic identifiers secured with public keys. This means that even if a node along the route is compromised, your data remains protected.
Uni-directional tunnels: I2P employs uni-directional tunnels, separating incoming and outgoing traffic. This setup enhances privacy by allowing senders and recipients to communicate without revealing their IP addresses, thanks to the presence of inbound and outbound proxy routers.
Garlic routing: Unlike Tor's onion routing, I2P utilizes garlic routing. This method divides your message into smaller encrypted segments known as cloves. These cloves travel independently to their destinations, making it exceptionally difficult for interceptors to piece together the entire message and perform traffic analysis.
Decentralization: The strength of I2P lies in its decentralization. Spread across thousands of devices worldwide, I2P doesn't rely on a single entity. Even if one device is compromised, it doesn't jeopardize the entire network's security.
I2P vs Tor

In Tor, the entry node can see your real IP address but not the content of your data or your online activities. If you access the regular internet through Tor, the exit node decrypts and re-encrypts your data, gaining visibility into the websites you visit but remaining unaware of your real IP address. However, with Tor onion services (the dark web), there's no exit node; onion sites exist solely within the Tor network.
Now, let's explore how I2P distinguishes itself with its garlic routing system:
Garlic routing: Unlike Tor's method, I2P bundles data packets into cloves before transmission. Each message typically contains one clove, sometimes two. This clove bundling makes it tougher for attackers to perform timing attacks, enhancing user anonymity. Moreover, it theoretically boosts network efficiency, potentially resulting in faster page loading times.
Unidirectional traffic: While Tor employs bidirectional traffic, I2P utilizes unidirectional traffic. Outgoing and incoming data travel along different paths, complicating attempts to trace connections back to users.
Short-lived tunnels: I2P adopts short-lived tunnels, in contrast to Tor's longer-lived ones. This setup adds another layer of difficulty for potential attackers targeting connections.
Packet switching: Unlike Tor's circuit switching, I2P employs packet switching, offering advantages in load balancing and resilience. While theoretically promising better scalability, Tor has already addressed some scaling issues that I2P is still working on.
I2P vs VPN

When comparing I2P with VPNs, it's essential to understand their respective purposes and functionalities. While I2P and Tor excel in providing extreme anonymity, they may slow down your internet traffic. For everyday use where such high levels of privacy aren't necessary, opting for a VPN might be a simpler and more effective solution.
A VPN, or Virtual Private Network, offers robust encryption to safeguard your data and privacy by masking your IP address. It achieves this by routing your encrypted traffic through remote servers, preventing any potential interceptions. Additionally, VPNs are incredibly user-friendly and typically have minimal impact on your internet speed, making them a convenient choice for everyday online activities.
Pros and Cons of I2P
I2P offers a blend of advantages and drawbacks worth exploring:
Pros:
- Enhanced security. I2P provides robust protection against hackers, third-party surveillance, and interception attempts. Its garlic routing system ensures that data traveling through the network is challenging to decipher, reducing the risk of man-in-the-middle attacks and bolstering overall security.
- Efficient performance. Leveraging packet switching, I2P distributes traffic balancing across different peers, enhancing performance efficiency. This design minimizes the likelihood of peer overload and ensures seamless operation even if some peers are malfunctioning.
- Privacy enhancement. Utilizing an I2P tunnel affords users greater privacy, shielding them from the prying eyes of companies seeking to monitor and exploit their data. This safeguard reduces the amount of personal information accessible to internet service providers and advertisers, safeguarding personal privacy.
Cons:
- Complex installation and usage. Setting up and using I2P entails a relatively intricate installation process and browser configuration.
- Mandatory logging. Users must remain logged in to the system for their content to be accessible, potentially compromising anonymity and privacy.
- Limited anonymity on indexed sites. While I2P excels in preserving anonymity within its network, browsing indexed sites on the surface web may compromise privacy. Using VPN protection alongside I2P can mitigate this limitation.
- Smaller user base. Compared to Tor, I2P has a smaller user base and fewer network nodes, making it marginally more susceptible to attacks. However, ongoing development efforts aim to address and mitigate these vulnerabilities.
How to set up I2P?
Setting up I2P on your desktop is a straightforward process.
- Begin by downloading and installing the I2P router software. You can find versions for Windows, macOS, and Linux. If you're installing on Linux, make sure you have Java installed as well.
- Once the installation is complete, your default browser will automatically open the I2P Router Console page. If it doesn't, you can access it by entering "127.0.0.1:7657" in your browser's address bar while the I2P router service is running.
- The Router Console page allows you to manage and configure your I2P server. Here, you'll find links to various I2P resources, including FAQs, technical documentation, and community websites. You can also access I2P's built-in applications such as address book and email, BitTorrent, and web server apps.
- To access eepsites (I2P websites), you'll need to configure your browser's proxy settings to route traffic through I2P. Instructions for configuring proxy settings can usually be found within your browser's settings menu.
On Android:
- You can download the I2P app from the Google Play Store, F-Droid, or as an APK file. Once installed, open the app to begin setup.
- Similar to the desktop version, the I2P app allows you to manage and configure your I2P server settings directly from your Android device.
- Since modern versions of Chrome and Firefox for Android don't support manual proxy configuration, you'll need to use open-source Android browsers that do. The I2P app provides instructions for configuring these browsers to route traffic through I2P.
How to use I2P?
Using I2P for browsing regular websites isn't its primary purpose, and we advise against it. Instead, I2P is designed for accessing eepsites, which are websites hosted within the I2P network. Here's how you can use I2P to explore these eepsites:
- Start by using I2P Search, a search engine designed for the I2P network, to find eepsites. This search engine indexes content specifically within the I2P network, making it a reliable starting point for discovering eepsites.
- If you come across an eepsite that isn't already listed in your Addressbook, you may need to use a jump service to connect to it. Jump services act as bridges between the clear web and the I2P network, allowing you to access eepsites that may not be directly accessible.
- Once you've found an eepsite that interests you, you can add it to your Addressbook for easy access in the future. This way, you won't need to rely on jump services every time you want to visit the site.
However, it's essential to note that many eepsite links may no longer be active. Over time, some eepsites may become inactive or inaccessible, so be prepared to encounter dead links during your exploration of the I2P network.
Conclusion
I2P offers a secure and anonymous way to communicate and browse the internet. By encrypting and routing data through a decentralized network, I2P ensures privacy and protection from surveillance. Its innovative features like garlic routing and end-to-end encryption make it a valuable tool for individuals seeking to safeguard their online activities.




Comments 0