
The Tor Browser is an invaluable tool for those who prioritize privacy and security on the internet. By routing user traffic through multiple layers of encryption across several nodes worldwide, Tor provides anonymity and access to the uncensored web. However, these additional layers of security can also lead to slower browsing speeds.
- Tor network
- The purpose of Tor
- Why is the Tor Browser slower than regular browsers?
- How can you make the Tor Browser run faster?
- What is the maximum speed of the Tor Browser?
- Which is better for privacy and security: Tor or VPN?
- Conclusion
Tor network
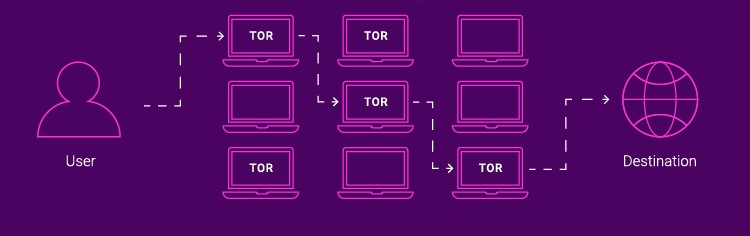
Before diving into optimization techniques, it’s important to grasp how the Tor network operates.
Tor anonymizes user data by routing it through a distributed network of relays run by volunteers around the globe. This process involves three key types of nodes: entry (guard) nodes, middle (relay) nodes, and exit nodes.
- Entry nodes: When you initiate a connection using Tor, your data first reaches an entry node, also known as a guard node. This node sees your real IP address but does not know the final destination of your data.
- Middle nodes: From the entry node, the data is passed to one or more middle nodes. These nodes shuffle the data further, adding layers of encryption, and ensure that each node only knows the location of the previous node and the next one, but not the full path of the data.
- Exit nodes: Finally, the data reaches an exit node. This node removes the final layer of encryption and sends the data to its destination on the regular internet. The exit node knows the data’s final destination but does not know the source of the data, thereby disassociating your identity from your browsing activities.
Each relay in the Tor network peels away a single layer of encryption before passing the data to the next relay. This is akin to peeling an onion, which is where the name "The Onion Router" comes from. The layered encryption ensures that no single node on the network knows both the origin and destination of the data. This method provides strong anonymity but can result in slower connection speeds due to the multiple hops and layers of encryption.
The purpose of Tor
The primary purpose of the Tor network is to protect the privacy of users and enable anonymous communication. Here are some of the uses and benefits of Tor:
- Privacy and anonymity: Tor is crucial for users who wish to keep their browsing habits private from advertisers, ISPs, and governments.
- Circumventing censorship: Tor allows users to bypass governmental censorship, accessing the full range of information available on the internet without restriction.
- Sensitive communication: Journalists, activists, and whistleblowers can use Tor to communicate more safely with sources or to report on issues without fear of reprisal.
While Tor is highly effective in ensuring privacy and bypassing censorship, it has some limitations:
- Speed: Due to the extensive routing and encryption process, browsing on Tor can be slower compared to conventional browsers.
- Complexity: Setting up and using Tor correctly requires more technical knowledge than typical web browsing.
- Blocked services: Some websites block traffic from known Tor exit nodes due to abuse or to prevent anonymous access.
Why is the Tor Browser slower than regular browsers?

The Tor Browser is renowned for its ability to provide privacy and anonymity online, but it's also often noted for its slower browsing speed compared to standard browsers. This reduced speed is a trade-off for the enhanced security features and complex data routing protocols it employs to protect user identity and activity. To understand why the Tor Browser operates at these slower speeds, we must examine the structural and functional elements that underpin its design.
Multi-layered encryption
Tor Browser protects data by wrapping it in multiple layers of encryption. Each layer corresponds to a segment of the network path through which the data will travel. As data passes through each relay in the Tor network, a layer of encryption is peeled off to reveal the next destination. This process ensures that no single relay knows both the origin and final destination of the data, significantly enhancing security. However, the time taken to encrypt and decrypt the data at each relay contributes to slower browsing speeds.
Circuitous routing
Unlike conventional direct routing used by most internet services, Tor's routing is intentionally circuitous. Data packets on the Tor network take a convoluted path through a series of relays, which can span multiple countries and continents. Each relay only knows the location of the previous and the next relay, not the endpoints of the data journey. While this protects the user's anonymity by obfuscating the path and origin, it also means that data often travels much farther than it would over the standard internet, thereby increasing transit time and reducing speed.
Relay performance variability
The Tor network is maintained by volunteers who run relays on their own servers. These relays vary significantly in terms of bandwidth and load capacity. Some relays might be running on high-performance servers with dedicated connections, while others might be operating on modest setups with limited bandwidth. This variability can affect the consistency of the browsing experience, as the speed of the Tor Browser is contingent upon the slowest relay in the path.
Network congestion
Tor's design also makes it susceptible to network congestion. Since all data must pass through at least three nodes (entry, middle, and exit), the performance of each node impacts overall speed. During peak times, when many users are accessing the network, congestion can occur, leading to delays and slower speeds. Moreover, the growing popularity of Tor as a tool for privacy-conscious individuals means that network congestion issues are more likely to occur as the user base expands.
Security measures
The Tor Browser includes various integrated security features designed to prevent tracking and malicious attacks. These include disabling certain types of scripts and functionalities that could compromise user privacy. While these security measures are crucial for safe browsing, they can also restrict some of the dynamic content on websites, leading to slower loading times or limited functionality of web pages.
How can you make the Tor Browser run faster?

Making the Tor Browser run faster involves balancing the intrinsic trade-offs between privacy, security, and speed. Below, we explore several practical steps that can help optimize the performance of your Tor Browser, while still maintaining a focus on security and anonymity.
1. Update the Tor Browser
Regular updates to the Tor Browser include performance enhancements, security updates, and new features that can improve speed. Ensure that your browser is always updated to the latest version to benefit from these improvements.
2. Use a bridge relay
Bridge relays are Tor relays that are not listed in the public Tor directory, making it harder for ISPs to block or throttle them. Using a bridge can sometimes help you bypass network restrictions and improve speed, especially in regions where Tor use is restricted or monitored.
3. Use a wired internet connection
Wireless connections can be unstable and slower compared to wired connections. Using a wired internet connection can reduce latency and increase the reliability of your connection, thereby potentially enhancing the speed of the Tor Browser.
4. Optimize your device
Ensure that your device is running optimally by closing unnecessary applications and tabs that may be consuming system resources. A well-optimized machine can handle Tor’s encryption and decryption processes more efficiently, improving overall performance.
5. Create a new Tor circuit
If you are experiencing slow speeds, you can request a new Tor circuit for your current site. This can be done by clicking on the onion icon in the toolbar and selecting "New Circuit for this Site". This action will reroute your connection through a different set of relays, which might be faster.
6. Use new identity
Using the "New Identity" feature will close all your open tabs and windows, clear all private information such as cookies and history, and use a new Tor circuit. This can help if the current identity is experiencing slow connections or if you believe your current circuit is being throttled.
7. Try Tor on Brave Browser
The Brave Browser offers a Tor mode in a tab that might run differently from the Tor Browser. While it may not offer the same level of privacy as the Tor Browser, it can be a useful alternative for users looking to balance speed with some level of privacy.
8. Replace the old torrc file with the new one
The torrc file contains configurations for the Tor software. If you suspect your configurations might be outdated or improperly set up, replacing the old torrc file with a new, default one can reset your settings to a potentially more optimized state. Be sure to back up your current torrc file before replacing it, in case you need to revert to your original settings.
By implementing these steps, you can enhance the performance of your Tor Browser. While Tor will generally not match the speed of less secure browsers due to its complex, privacy-focused architecture, these optimizations can help make your browsing experience more efficient.
What is the maximum speed of the Tor Browser?
In theory, the maximum speed of the Tor Browser is limited by the slowest relay in your circuit. If all the relays in your chosen path are high-speed and the network is not congested, your browsing speed could approach that of a regular internet connection, minus the delays introduced by the encryption and decryption processes at each relay.
However, such ideal conditions are rare. In practice, users often experience speeds that are significantly lower than their normal broadband or mobile data speeds due to the aforementioned factors.
For users, it is more practical to focus on what speeds are realistically achievable rather than a theoretical maximum. Speeds on the Tor network can vary from very slow, sometimes just enough to handle basic browsing and email, to moderately fast, where streaming of low-resolution video becomes feasible. The variability is a direct consequence of the network’s structure and the random path that your data takes through the relays.
Which is better for privacy and security: Tor or VPN?

When considering whether Tor or a VPN (Virtual Private Network) is better, it's essential to recognize that both technologies offer privacy and security but serve different needs and use cases.
Tor
- Tor provides superior anonymity by routing your traffic through multiple nodes, each of which only knows the IP address immediately before and after it in the network. This makes it extremely difficult for anyone to trace your activity back to you, making Tor highly effective for those prioritizing anonymity.
- The Tor network typically experiences slower speeds due to the layered encryption and the circuitous route that traffic takes through multiple relays across the globe.
- Using Tor can be as simple as downloading and installing the Tor Browser, which is configured to use Tor right out of the box. However, Tor can be slower and does not automatically encrypt other applications' traffic outside of the browser.
- Tor is very secure against network surveillance that threatens personal freedom and privacy. However, it is not designed to protect data from end-to-end. Data exiting the Tor network can be intercepted if not encrypted with HTTPS.
- Ideal for those needing to avoid tracking, surveillance, or censorship without leaving traces of their internet use, such as journalists, activists, or those in heavily restricted regions.
VPN
- VPNs encrypt your internet traffic and route it through a server owned by the VPN provider. This hides your real IP address from websites and eavesdroppers but does not provide the same level of anonymity as Tor, since the VPN provider can see your traffic and log your activity if they choose.
- VPNs generally offer faster connections than Tor because they usually involve a single encryption layer and direct routing. This makes VPNs more suitable for bandwidth-intensive activities like streaming and downloading large files.
- VPNs are straightforward to use, requiring just an app from the service provider that works across your devices and encrypts all internet traffic, not just browser activity. This makes it easy to secure all data transmissions.
- VPNs secure your entire internet connection with strong encryption, which protects your data from eavesdroppers. However, the security largely depends on the protocols the VPN provider uses and their policies on logging user activity.
- Best suited for users looking to secure their online activities from local snoopers like ISPs or in public Wi-Fi scenarios, or for those who want to bypass geo-restrictions on content.
Using a VPN with Tor, known as "Tor over VPN", enhances privacy and security more effectively than using either technology separately. This setup masks Tor usage from ISPs, bypasses Tor restrictions, and provides an additional layer of security by preventing Tor entry nodes from seeing your real IP address. This combination is especially beneficial for users in restrictive environments or those who prioritize maximum anonymity online.
Conclusion
Enhancing the speed of the Tor Browser involves a thoughtful blend of technical adjustments and practical usage strategies. While Tor is inherently slower than conventional browsers due to its focus on privacy and security through multi-layered encryption and circuitous routing, users can adopt several measures to optimize their experience. Regularly updating the Tor Browser, utilizing bridge relays, opting for wired internet connections, and ensuring device optimization are all proactive steps that can contribute to improved performance. Additionally, creating new Tor circuits and refreshing identities can help circumvent slower nodes and reduce lag.
It’s important to remember that the very features that may slow down the Tor Browser also make it a powerful tool for protecting personal privacy against tracking and surveillance. Users of Tor are encouraged to weigh the trade-offs between speed and security based on their individual needs and the sensitivity of their online activities.





Comments 0