
The Dark Web represents one of the most enigmatic and misunderstood facets of the internet. Shrouded in anonymity, it operates beyond the reach of standard search engines and conventional online browsing, fostering a realm where privacy is paramount, and activities—both noble and nefarious—flourish away from the public eye. This hidden segment of the internet, while often associated with illegal activities, also serves as a critical sanctuary for free speech, privacy advocacy, and circumvention of censorship.
The History and Evolution of the Dark Web
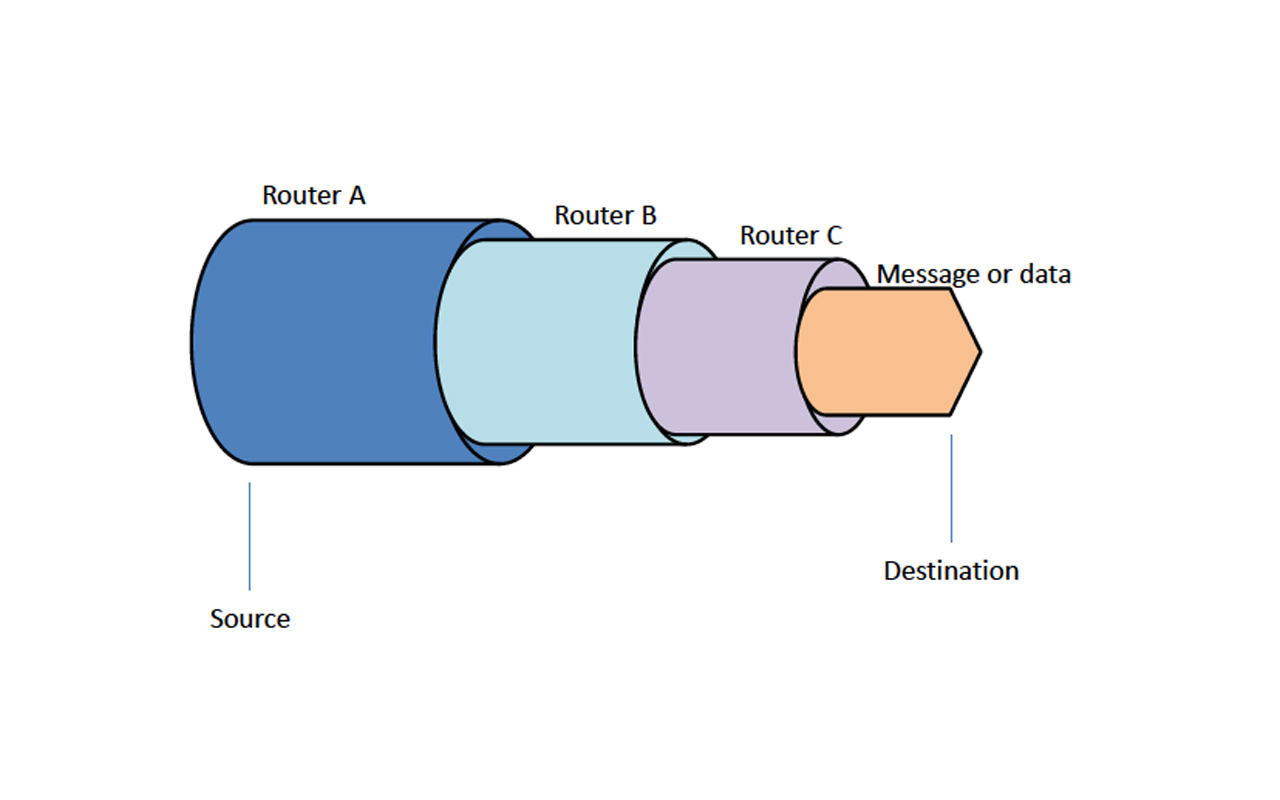
The foundational technology behind the Dark Web is The Onion Router (Tor), which was originally developed in the mid-1990s by mathematicians and computer scientists Paul Syverson, Michael G. Reed, and David Goldschlag at the United States Naval Research Laboratory. The initial purpose of Tor was to protect U.S. intelligence communications online by routing traffic through multiple servers and encrypting it at each step to make it untraceable.
Tor was released to the public in 2002 as an open-source project, enabling individuals outside of the government to communicate anonymously. The architecture of Tor made it ideal for creating hidden services, which are websites that can only be accessed through the Tor network, ensuring the anonymity of both the host and the user. These hidden services are what constitute a significant portion of what is known today as the Dark Web.
As awareness of digital privacy issues grew, so did the use of Tor and the Dark Web. It wasn't long before activists, whistleblowers, and those under oppressive regimes began to use it as a tool for circumventing censorship and safeguarding their communications. The Arab Spring in the early 2010s, for example, saw a significant rise in the use of Tor to bypass government blocks on social media and organize protests. However, the anonymity provided by the Dark Web also attracted illegal activities.
Today, the Dark Web is a complex ecosystem comprising legitimate uses, such as journalism, secure communication, and privacy protection, alongside illegal marketplaces and cybercriminal activities. The development of additional privacy-focused tools and networks, such as I2P and Freenet, has further diversified the ways in which users can access and host content anonymously.
Deep Web vs. Dark Web
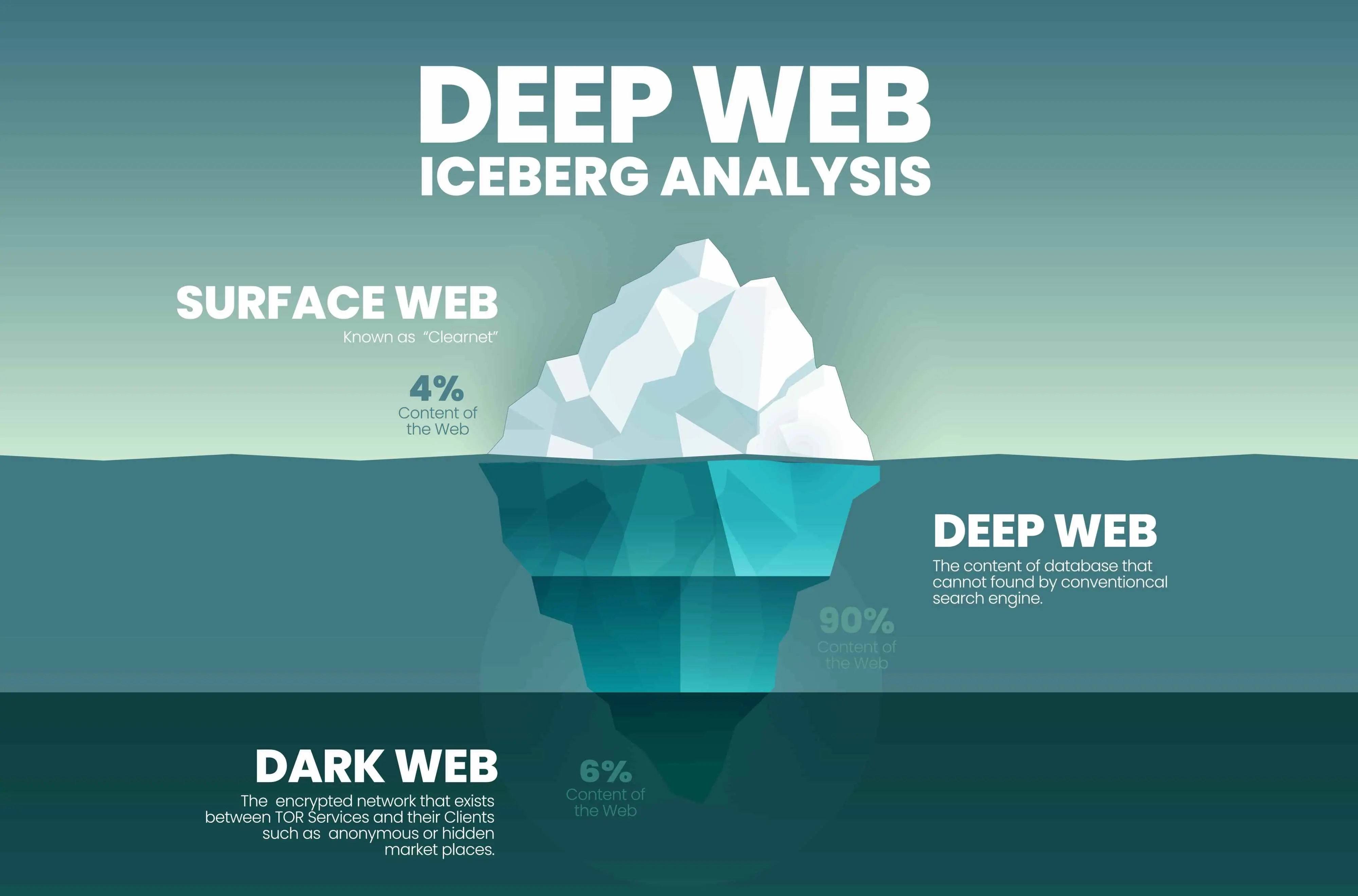
The terms "Deep Web" and "Dark Web" are often used interchangeably, but they refer to distinctly different parts of the internet.
The Deep Web encompasses all parts of the internet that are not indexed by traditional search engines like Google, Bing, or Yahoo. This includes a vast array of content such as private databases, academic journals, government records, corporate intranets, and more. Essentially, it comprises the majority of the web's content, vastly overshadowing what is accessible through standard web searches.
Key characteristics of the Deep Web include:
- Sheer size: The Deep Web is estimated to be several times larger than the surface web, containing an overwhelming majority of all information stored online.
- Privacy and security: Access to content on the Deep Web is often protected by passwords and encryption, ensuring that personal, corporate, or governmental information is secure and accessible only to authorized users.
- Dynamic content: A lot of the Deep Web consists of databases and content that are dynamically generated and thus cannot be indexed by conventional search engines.
The Dark Web is a subset of the Deep Web that has been intentionally hidden and is inaccessible through standard web browsers. It requires specific software, configurations, or authorization to access, with the Tor network being the most common entry point. The Dark Web is known for its emphasis on anonymity and privacy, often associated with both legitimate and illicit activities.
Key features of the Dark Web include:
- Anonymity: Tools like Tor and I2P anonymize user traffic, making it difficult to trace activity back to individuals, thereby fostering a sense of privacy and security for users.
- Illicit marketplaces: The Dark Web hosts numerous marketplaces that offer illegal goods ranging from drugs to counterfeit money, stolen data, and more. However, it's crucial to note that not all activity on the Dark Web is unlawful.
- Safe haven for activism: It also serves as a platform for political dissidents, whistleblowers, and journalists to communicate securely, away from the prying eyes of oppressive governments or corporate surveillance.
While both the Deep Web and the Dark Web are parts of the internet not readily accessible or indexed by standard search engines, the key difference lies in their accessibility and the nature of the content they host. The Deep Web is a vast reservoir of restricted-access content that is not meant for public view, primarily for reasons of privacy and security. In contrast, the Dark Web is specifically designed for anonymity and can host a mix of both legal and illegal activities. The common thread between them is their non-indexed status, keeping them beneath the surface of the conventional internet.
Tools and Services of the Dark Web

The Dark Web offers a variety of tools and services designed to maintain privacy, enhance security, and facilitate anonymous communication and transactions. These tools are not inherently illegal; they are designed to provide anonymity and protect user data in an environment where privacy is a priority. Below is an overview of some of the most notable tools and services associated with the Dark Web.
1. Tor Browser
The Tor (The Onion Router) Browser is the primary gateway to accessing the Dark Web. It anonymizes users' web traffic by routing it through a series of distributed nodes, effectively encrypting the data multiple times and masking the user's IP address. This makes it extremely difficult to trace the activity back to the user, providing a high degree of privacy and security.
2. I2P (Invisible Internet Project)
I2P is another privacy network layer that allows for secure and anonymous communication across the internet. It uses a peer-to-peer approach, creating a private network layer that can be used for secure messaging, browsing, and file sharing. Unlike Tor, which is optimized for anonymous web browsing, I2P is geared more towards creating a secure network for hosting services and communicating in a hidden manner.
3. Freenet
Freenet is a decentralized, censorship-resistant communication platform that allows users to anonymously share files, browse, and publish "freesites" (websites accessible only through Freenet). It operates by pooling the bandwidth and storage of member's computers to create a robust network that protects users' privacy and freedom of speech.
4. Cryptocurrencies
Cryptocurrencies, such as Bitcoin, Monero, and Zcash, are often used for transactions on the Dark Web due to their ability to facilitate secure and anonymous payments. Monero and Zcash, in particular, are favored for their enhanced privacy features, which make transactions nearly impossible to trace compared to the more transparent Bitcoin blockchain.
5. Secure messaging apps
Various secure messaging applications that prioritize end-to-end encryption and anonymity are also popular on the Dark Web. Examples include Signal, Wire, and Element, which offer encrypted communication to ensure that messages remain private and secure.
6. VPNs (Virtual Private Networks)
While not exclusive to the Dark Web, VPNs are often used in conjunction with Tor and other anonymity tools to add an additional layer of security and privacy. A VPN encrypts all internet traffic from a device and routes it through an intermediary server in a location of the user's choosing, masking the user's IP address and protecting their data from snooping.
7. Secure Drop
Secure Drop is a whistleblower submission system that media organizations can install to safely receive documents from anonymous sources. It's designed to protect the identities of whistleblowers by allowing them to share information without fear of retaliation.
8. Privacy-focused search engines
Search engine like DuckDuckGo is designed to offer users search capabilities without tracking their search history or behavior. DuckDuckGo is accessible on the surface web but is also available as a hidden service on the Tor network.
How to Access the Darknet?

Accessing the Dark Web safely and securely requires a few critical steps and tools, primarily focused on preserving your anonymity and protecting your device from potential threats. Below is a detailed guide on how to access the Dark Web:
1. Understanding the risks
Before diving into the Dark Web, it's crucial to understand the potential risks involved, including exposure to illegal activities, potential threats to your privacy, and the risk of downloading malicious software.
2. Using a VPN
Start by securing your internet connection with a Virtual Private Network (VPN). A VPN encrypts your internet traffic and masks your IP address, providing an additional layer of privacy and security. By connecting to a VPN before accessing the Dark Web, you help protect your identity and reduce the risk of being tracked.
3. Downloading Tor Browser
The primary tool for accessing the Dark Web is the Tor Browser, which can be downloaded for free from the official Tor Project website. Ensure you download the latest version to benefit from up-to-date security features.
- Go to the Tor Project website: https://www.torproject.org/
- Choose the version compatible with your operating system (Windows, macOS, Linux).
- Follow the installation instructions provided on the site.
4. Configuring Tor Browser settings
Upon first launching the Tor Browser, you may need to configure connection settings, especially if you're in a country with restricted internet access or if you're using a personal firewall or VPN. In most cases, however, the default settings should suffice.
5. Browsing Dark Web sites
Once the Tor Browser is installed and running, you can access Dark Web sites. These sites typically have .onion domains, which are not indexed by standard search engines and can only be accessed through the Tor network.
- Start by visiting known .onion directories or indexes to find Dark Web sites. Examples include "Deepweb" or "The Hidden Wiki," which lists various Dark Web sites across different categories.
- Always verify the authenticity of the sites you wish to visit to avoid phishing attempts or malicious content.
By following these steps and exercising caution, you can access the Dark Web safely. However, remember that navigating this part of the internet carries inherent risks, and it's crucial to stay informed about the best practices for online privacy and security.
Is the Dark Web Illegal?
Accessing the Dark Web in itself is not illegal. The Dark Web is a part of the internet that is intentionally hidden and requires specific software, configurations, or authorization to access. It uses strong encryption to anonymize users' identities and their online activities, offering a high level of privacy and security. This part of the web is often associated with illicit activities due to its anonymous nature, but the technology and networks that make up the Dark Web are not illegal.
However, the legality of actions performed on the Dark Web depends on the nature of those actions and the jurisdiction under which they fall. While the Dark Web can be used for legitimate purposes such as protecting privacy, free speech, and circumventing censorship, it has also been used for illegal activities, including drug trafficking, sale of stolen data, distribution of child pornography, and other criminal actions. Engaging in or facilitating such illegal activities is against the law, regardless of whether they are conducted on the Dark Web or elsewhere.
Conclusion
Dark Web is a complex and multifaceted part of the internet that remains shrouded in mystery and often misunderstood by the general public. Its foundations in privacy and anonymity technologies offer crucial benefits for safeguarding freedom of speech, protecting personal privacy, and enabling secure communication, especially in environments where these are compromised. However, the Dark Web's capacity to anonymize users and activities also presents significant challenges, as it can facilitate illegal and harmful activities.
It's clear that the Dark Web will continue to evolve, as will the tools and methods for accessing it, the nature of activities it hosts, and the legal and ethical frameworks governing its use.




Comments 0