
The Deep Web, also known as the invisible web, constitutes a clandestine network of websites that elude detection by conventional search engines, requiring access through specialized browsers. Regrettably, it remains a considerably misunderstood realm, frequently conflated with the Dark Web, owing to inaccuracies in media coverage and distortions in portrayals on television and in film.
Contrary to popular misconceptions, the Deep Web serves as a hub for numerous legitimate activities. Chances are, you've interacted with the Deep Web on multiple occasions today alone, whether it be checking your bank account, perusing emails, or accessing confidential documents.
What sets the Deep Web apart is not only its hidden nature but also its sheer magnitude, eclipsing the more visible surface of the web. Attempting to quantify its size precisely proves challenging, but experts posit that the Deep Web might surpass the Normal Web by a staggering factor of 500. In essence, it operates as an expansive and crucial component of the internet landscape, far beyond its mystique and commonly held misconceptions.
Understanding the Deep Web

The Deep Web constitutes a multifaceted realm on the Internet that evades detection and accessibility through conventional channels such as popular search engines or major web browsers. Its content remains beyond reach due to either partial indexing by search engines or the imposition of password protection measures.
Within the expansive confines of the Deep Web, a diverse array of information and data resides, shielded from the prying eyes of public scrutiny. Social media pages, emails, personal financial records, and confidential health reports are seamlessly integrated into the Deep Web, concealed from the gaze of popular search engines. Likewise, content secluded behind paywalls, ranging from exclusive movies to subscription-based stories, coexists within the territories of the Deep Web.
The inherent advantage of unindexed content becomes apparent in the preservation of privacy.
It is crucial to recognize that while certain segments of the Deep Web remain less accessible as a protective measure for the security of users and organizations, other portions deliberately cloak themselves to obscure illicit activities. This enigmatic facet, occupying the darker recesses of the Deep Web, is aptly denoted as the Dark Web — domain where covert and potentially criminal operations seek refuge. The Deep Web, thus, emerges as a nuanced space.
Distinguishing between the Deep Web and Surface Web
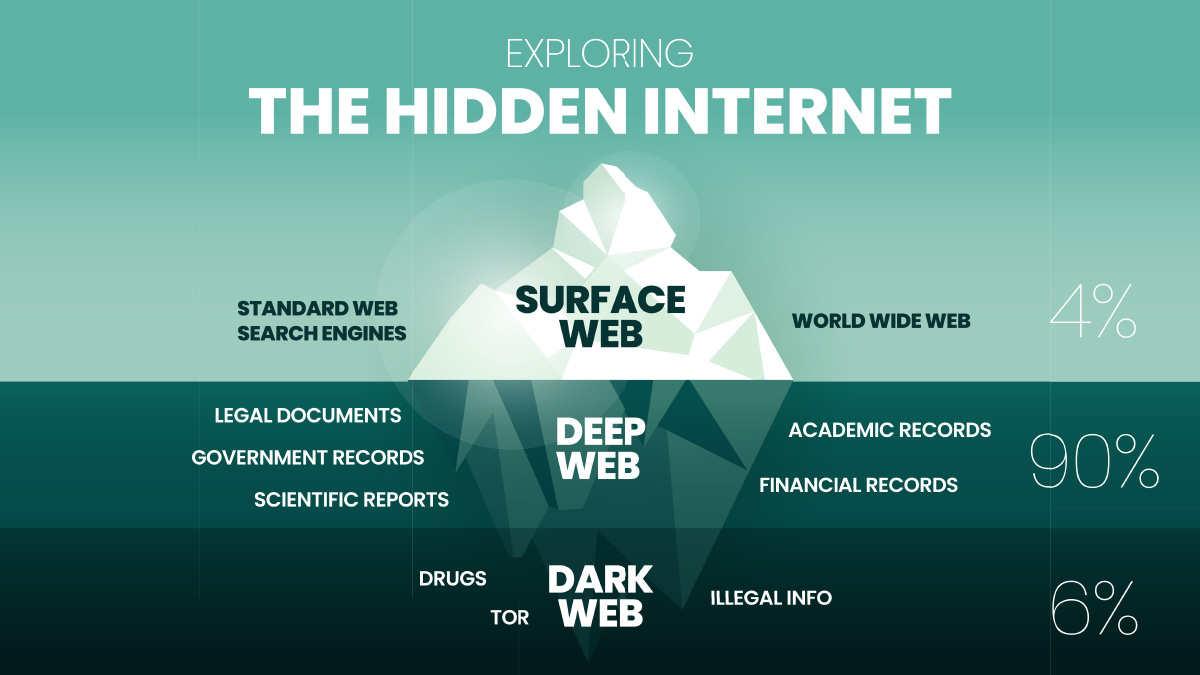
An analogy often used to depict the digital landscape is comparing the Internet to an iceberg, where the Surface Web represents the visible tip, and the expansive Deep Web lies submerged beneath. Alternatively, envisioning space exploration with an incomplete map provides another perspective – known locations discovered by explorers equate to the Surface Web, while undocumented or concealed locations comprise the Deep Web.
The integration of web content into the Surface Web involves the deployment of web crawlers by search engines like Google, Yahoo, and Bing. These digital explorers traverse the vast expanse of the World Wide Web, indexing its content for public access.
It is worth noting that many users encounter content on the Deep Web through the Surface Web. For instance, accessing an email account on the web involves being on the Surface Web when visiting the email’s webpage. However, the transition to the Deep Web occurs when accessing the account using login credentials, emphasizing the interconnected nature of these digital realms.
Deep Web and Dark Web

The Deep Web, primarily concealed to safeguard lawful content, constitutes a realm intentionally kept invisible from unauthorized access. As elucidated earlier, content residing in the Deep Web avoids indexing by search engines and encompasses a spectrum that includes password-protected websites, pages secluded behind paywalls, and private communications such as emails and social media messages.
Drawing a distinction between the Deep Web and the Dark Web involves conceptualizing the former as the imperceptible segment of the Internet, while the latter is envisioned as the clandestine recesses of the digital realm. While both spaces can host both legal and illicit activities, the Deep Web typically serves as a haven for legitimate endeavors, contrasting sharply with the Dark Web's notoriety for fostering illegal activities.
It's important to note that the Dark Web is only a minuscule fraction within the expansive landscape of the Deep Web, yet it holds a reputation for being a hub of some of the most high-friction and illicit activities on the web.
Access to the Deep Web
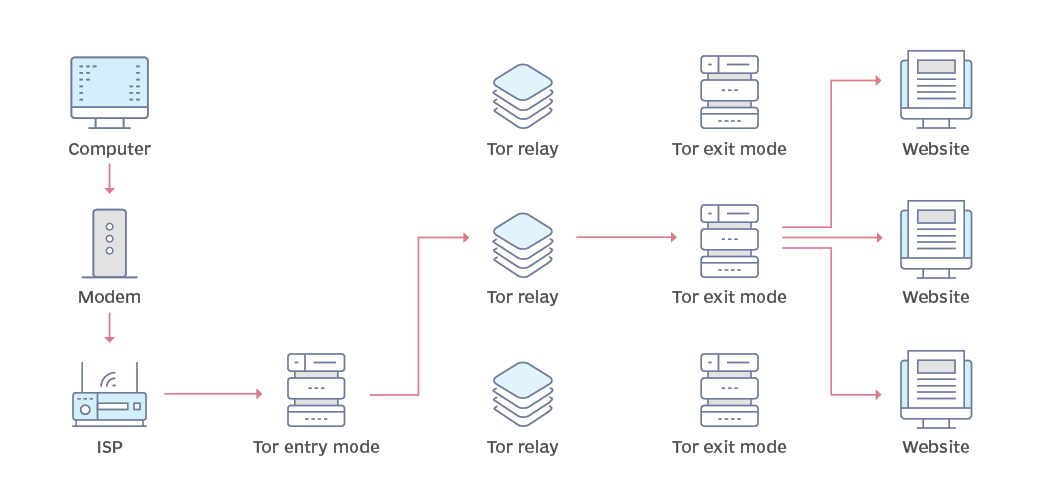
Accessing the information housed in the deep web, while not indexed by conventional search engines, remains a relatively common practice for internet users. Contrary to misconceptions, engaging with content on the deep web is generally secure, with routine activities like logging into Gmail, accessing LinkedIn, or signing in to read articles on the Wall Street Journal constituting examples of everyday deep web interactions.
It is crucial to recognize that user accounts on the deep web often store substantial amounts of personal information, contributing to the restricted access enforced in many instances to protect against potential misuse by criminals.
Distinguishing itself from the accessible deep web, the dark web operates on intentional obscurity and necessitates specific technologies, such as the Tor browser and the Invisible Internet Project (I2P) network, for entry. These tools, designed for legitimate purposes, serve functions such as protecting user IP addresses and providing a proxy network for journalists reporting from precarious territories.
Notably, access to a dark web marketplace is contingent on using the Tor browser, and while rooted in the Mozilla Firefox browser, Tor is not as well maintained and has page rendering issues. The intentional concealment of the dark web is reinforced by its need for specialized technologies.
Guidelines for secure Deep and Dark Web exploration

Exploring the realms of the Deep and Dark Web necessitates an approach to ensure safety and security. While a regular browser suffices for most segments of the Deep Web, delving into the Dark Web mandates the use of TOR for heightened anonymity and protection.
- Implementing robust protective measures for your network is paramount. Utilize both a firewall and a VPN to fortify your defenses. A VPN not only adds an extra layer of privacy by masking your IP address but also contributes to safeguarding your network integrity.
- Exercise caution and restraint when traversing these concealed digital spaces. Avoid temptation to explore illegal websites, as they may harbor malware, phishing traps, or disturbing content that could compromise your system's security.
- When downloading files, exercise discernment and only obtain them from sources you trust implicitly. Augment your defense mechanisms by employing anti-malware software to shield your computer from potential threats lurking in the digital shadows.
- To fortify your privacy, consider disconnecting your microphone and webcam during your excursions into these territories. Employing a free anti-spyware scanner and removal tool afterward can serve as an additional layer of protection, checking your system for any traces of spyware, stalkerware, or keyloggers that may have been acquired during your exploration of unknown websites.
By adhering to these best practices, individuals can embark on a journey through the Deep and Dark Web with a heightened sense of security, minimizing the risks associated with the inherently complex and clandestine nature of these digital domains.



Comments 0