
In the current landscape dominated by concerns about data collection and privacy, the Tor browser has gained attention and a degree of notoriety. Similar to various clandestine elements on the internet, it remains somewhat enigmatic and surrounded by elements often associated with realms like hacking or cryptocurrencies.
Originally crafted by the U.S. Naval Research Lab during the 1990s, onion routers derive their name from the layering technique reminiscent of an onion, designed to obscure information regarding user activities and locations. Interestingly, the organization received a significant portion of its funding from branches of the United States government over the years, maintaining the perspective that Tor serves as a tool to promote democracy in authoritarian states.
To grasp how Tor safeguards a user's identity during internet browsing, it's essential to delve into the fundamental workings of the internet. At its core, the internet comprises connections between computers spanning vast distances. Some computers, known as servers, store the data accessible on the internet, including popular websites like Google. Devices used to access this information, such as smartphones or computers, are referred to as clients. The transmission lines linking clients to servers vary, from fiber-optic cables to Wi-Fi, constituting the intricate web of connections. With the advent of technologies like Wi-Fi, satellite internet, and portable hotspots, the internet has become both more accessible and, concurrently, more susceptible than ever.
Various methods can compromise data integrity, particularly if networks lack proper encryption or inadvertently acquire malware. On the positive side, individuals and entities, including governments, law enforcement, Internet Service Providers (ISPs), and social media companies, may access internet data for purposes such as monitoring illegal activities or gathering valuable insights into user behaviors for analysis or sale.
Numerous solutions have emerged to address these privacy concerns, such as Virtual Private Networks (VPNs). Tor stands out as another browser-based solution adopted by many.
Tor's approach to secure browsing
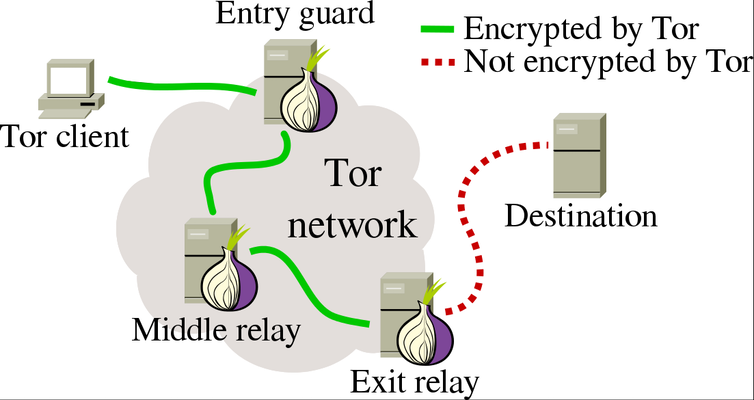
The efficacy of Tor in ensuring secure browsing hinges on two fundamental aspects of onion routing. Primarily, the Tor network relies on volunteers who offer their computers as nodes. During typical internet browsing, data moves in packets across the network. However, when a Tor user accesses a website, their packets do not follow a direct route to the server. Instead, Tor establishes a path through randomly assigned nodes that the packet traverses before reaching its intended destination.
The second crucial aspect of onion routing involves the construction of packets. Ordinarily, packets contain information about the sender's address and the destination, akin to conventional mail. In Tor, however, packets are enveloped in successive layers, resembling a nesting doll.
At each node, only the last and next destinations of the packet are known. No node retains the complete path of the data, and any observer monitoring the outbound message, provided the initial three servers are configured correctly, cannot discern the entire route.
Tor's user base and motivations

Understanding the demographics of Tor's user base is challenging due to the inherent anonymity the platform provides. However, certain trends emerge, and some users vocalize their reasons for choosing Tor.
Tor has gained traction among journalists and activists in nations with stringent internet and expression restrictions. For those in need of a secure channel to leak information, Tor offers a refuge. Notably, figures like Edward Snowden utilized Tor to disclose details about the NSA's PRISM program to news organizations.
Beyond activists and whistleblowers, Tor finds appreciation among academics and regular citizens alike, who view it as a tool to safeguard privacy and preserve freedom of expression in the digital era. Even intelligence agencies, such as the CIA, utilize Tor to facilitate the receipt of tips and information.
Despite the Tor Project's positive intentions, the platform has acquired a tarnished reputation in the mainstream media, not entirely without reason. The combination of being a freely accessible privacy browser, easily disseminated, and featuring support and community forums has led to the formation of communities around controversial subjects. Tor addresses this perception by organizing PrivChat webinars featuring influential users in human rights and democracy advocacy, and by providing guides for individuals navigating hostile governmental environments to ensure their safety.
Getting started with Tor
Aligned with the principles of the Tor Project, Tor is freely accessible and compatible with a variety of platforms, including Linux. The process involves a straightforward download and installation of the browser, obtainable from the Tor Project website. It's worth noting that the browser is a modified version of Firefox, catering to users of Windows, macOS, Linux, and Android.
While the Tor Browser comes pre-configured for seamless operation, individuals on networks equipped with firewalls or other security measures might encounter challenges. Additionally, maintaining caution during browsing remains crucial to preserving one's anonymity. Tor's official website provides a list of activities to avoid while utilizing the browser.
How to use Tor
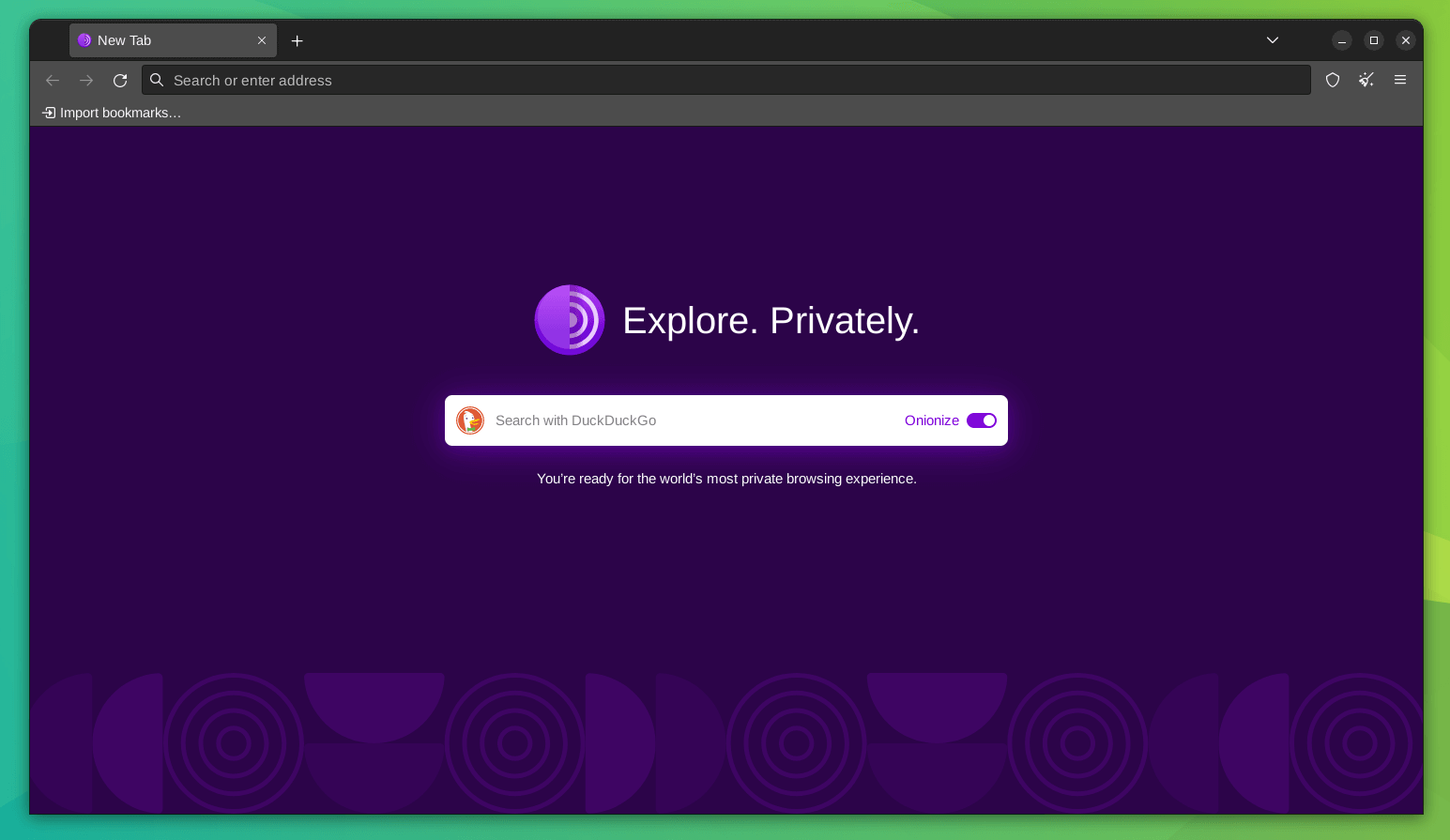
After successfully downloading and installing Tor Browser, familiarize yourself with its functionality using the following steps:
- Launch Tor Browser on your computer.
- On the Connect to Tor screen, opt to either connect immediately by selecting "Connect" or take the time to configure your connection by choosing the "Configure connection" option.
- It may take a few minutes to establish a connection. Once connected, a welcome screen featuring a DuckDuckGo search engine search bar will appear prominently. Utilize this search bar or the one at the top of the Tor Browser window for a more private web search. Enter your search terms in the address bar and press Enter, or click the Right arrow icon to access DuckDuckGo search results.
- Some websites operate as onion services, accessible only via the Tor network. To reach these onion service websites, enter their onion address (usually 56 characters ending with ".onion") into the address bar. Tor may display a purple ".onion available" icon in the address bar for regular websites offering an onion service version. Select it to access the onion service version.
- In the top-right corner of Tor Browser, between the menu icon and the Star bookmark icon, you'll find two icons: a shield and a broom. The shield allows you to choose the security level, while the broom signifies the New identity feature. This feature starts a new session, erasing all traces of the old/current session, including browsing history, as Tor Browser essentially restarts.
- Clicking the Three horizontal lines menu icon reveals a drop-down menu. Besides "New identity", you can select "New Tor circuit for this site". A circuit represents the pathway connecting a user to a website via Tor. If facing difficulties connecting to a website, restart the tab and attempt to load the site with a new circuit by selecting "New Tor circuit for this site". This feature doesn't delete private information.
A guide to finding onion websites in the Tor network

Locating onion websites in the Tor network involves a specific process, as these sites are designed to provide a higher level of anonymity and security. Here's a guide on how to find onion websites in the Tor network:
- Explore onion directories
Several onion directories exist on the internet, listing various onion websites. These directories serve as indexes for onion sites, making it easier for users to discover them. Examples include the DeepWeb (http://deepweb4wt3m4dhutpxpe7d7wxdftfdf4hhag4sizgon6th5lcefloid.onion/) and the Hidden Wiki (http://zqktlwiuavvvqqt4ybvgvi7tyo4hjl5xgfuvpdf6otjiycgwqbym2qad.onion/).
Access these directories using the Tor Browser and explore the categories or search functionalities they provide.
- Use search engines for the Dark Web
Specialized search engines for the dark web, such as "notEvil" (http://notevilmtxf25uw7tskqxj6njlpebyrmlrerfv5hc4tuq7c7hilbyiqd.onion/) or "Ahmia" (http://juhanurmihxlp77nkq76byazcldy2hlmovfu2epvl5ankdibsot4csyd.onion/), can help you discover onion websites.
Enter keywords or categories in these search engines to find relevant onion links.
- Visit forums and community boards
Dark web forums and community boards often share onion links. Websites like Breaking Bad forum (http://bbzzzsvqcrqtki6umym6itiixfhni37ybtt7mkbjyxn2pgllzxf2qgyd.onion/) or Dread (http://dreadytofatroptsdj6io7l3xptbet6onoyno2yv7jicoxknyazubrad.onion/) may contain discussions where users share and exchange onion links.
- Follow recommendations from trusted sources
Trustworthy sources within the Tor community may recommend onion websites. These recommendations can be found on social media, forums, blogs, or other platforms where security and privacy-focused individuals gather.
- Access .onion links from regular websites
Some regular websites also have corresponding onion service versions. Look for a purple ".onion available" icon in the address bar when browsing with the Tor Browser. This indicates that an onion service is available for the website you are visiting.
Conclusion
As technology evolves, so too does the landscape of online anonymity. The Tor network stands as a testament to the ongoing pursuit of privacy in the digital age. Whether you are seeking information, engaging in activism, or simply curious about the hidden corners of the internet, understanding how to find onion websites enhances your ability to navigate this unique and complex realm.
Remember, while the Tor network offers increased privacy, it does not guarantee complete anonymity. Users should prioritize their safety, stay informed about potential risks, and approach the exploration of the dark web with a responsible mindset.




Comments 0