Internet censorship represents the control or suppression of what can be accessed, published, or viewed on the internet by governments, corporations, or other entities. This practice varies widely across the globe, from minimal interference in some countries to strict regulations and monitoring in others. Its mechanisms and implications extend far beyond the mere act of restricting access to information; they touch upon fundamental issues such as freedom of speech, privacy, and the global exchange of ideas.
What is commonly censored?
Common targets of internet censorship reflect a broad spectrum of content, ranging from politically sensitive information to culturally or morally deemed inappropriate material. The nature of what is censored often mirrors the priorities, values, and fears of those wielding the power to restrict access. Here are some of the most frequently censored categories:
- Political content: Information that criticizes the government, exposes corruption, or advocates for political reforms is a prime target for censorship. Authoritarian regimes, in particular, may suppress dissenting views to maintain control and prevent opposition.
- Social issues: Discussions on human rights, minority groups, and gender equality can be sensitive topics for certain societies or governments. Content promoting social change or challenging traditional norms may be restricted.
- Religious content: Material that is perceived as offensive to religious beliefs or that promotes religious dissent is often censored in countries where religion plays a central role in societal norms and governance.
- Cultural content: Content that conflicts with national identity, cultural values, or moral standards can be subject to censorship. This includes literature, films, and art that diverge from accepted norms.
- Violence and pornography: Many governments regulate access to violent content and pornography to protect societal moral standards and, particularly, children. The degree of restriction can vary significantly from one country to another.
- Intellectual property violations: Copyright infringement, including unauthorized sharing of music, films, books, and software, is commonly censored to protect the rights of content creators, though the enforcement intensity can differ greatly.
- Misinformation and hate speech: In an effort to combat the spread of false information and protect public order, some governments and platforms restrict content deemed to be spreading lies, hate speech, or inciting violence.
- Security information: Content related to national security, military secrets, or information that could aid in criminal activities (such as hacking tutorials) is frequently censored to protect national interests and public safety.
Where is internet content censored?
Internet content can be censored at multiple levels, from individual devices to broader national policies, affecting what users can see, share, and access online.
- Blocks on your device. Software installed on personal devices, such as parental controls or enterprise management tools, can restrict access to specific websites, apps, and types of content based on settings chosen by parents, employers, or the device owner.
- Blocks on your local network. Organizations, schools, and households may implement filtering on their local networks to block access to certain internet content. This is often done to enforce policies, protect users from harmful content, or comply with institutional standards.
- Blocks at the ISP and national level. Internet Service Providers (ISPs) can block or throttle access to specific websites and services, either to comply with government regulations or to enforce their own network policies. At the national level, governments can mandate ISPs to censor certain types of content. This might include politically sensitive information, social media platforms, or sites that violate copyright laws.
- Blocks implemented by search engines. Search engines may remove or demote certain results from their listings due to legal requirements, copyright claims, or their own content policies. This type of censorship can affect the visibility of information and how easily users can find content online.
How does internet censorship work?

Internet censorship operates through a variety of technical mechanisms, each designed to control or restrict access to information online. These methods can be implemented by governments, ISPs, and organizations to filter out unwanted content, restrict certain websites, or monitor and shape internet traffic.
- DNS tampering. The Domain Name System (DNS) translates domain names into IP addresses that computers use to communicate. DNS tampering involves altering the responses from DNS servers so that the correct IP address is not returned for a domain, effectively preventing users from accessing certain websites. Users are either redirected to incorrect websites or encounter errors when trying to access blocked content.
- IP address blocking. Every server on the internet has a unique IP address. By blocking specific IP addresses at the router or ISP level, access to servers hosting undesirable content can be blocked. Even if the user knows the IP address of a website, they won’t be able to access it if the IP is blocked.
- URL filtering. This method involves scanning the full URL of a web request and comparing it against a database of blocked URLs. If a match is found, the request is denied. Specific pages or resources can be blocked without restricting access to the entire website.
- Filtering packets. Deep Packet Inspection (DPI) technology analyzes the data part (and possibly the header) of a packet as it passes an inspection point. DPI can be used to block, reroute, or log data packets with specific characteristics or content.
- Traffic shaping. Also known as bandwidth throttling, traffic shaping is the process of intentionally slowing down internet traffic based on the type of content being transmitted.
- Port number blacklisting. Internet applications use specific port numbers to communicate over the network. By blocking or restricting access to specific port numbers, ISPs or network administrators can prevent the use of certain applications or protocols.
These mechanisms can be used individually or in combination to enforce internet censorship, with varying degrees of effectiveness and intrusiveness.
How can you bypass internet censorship?
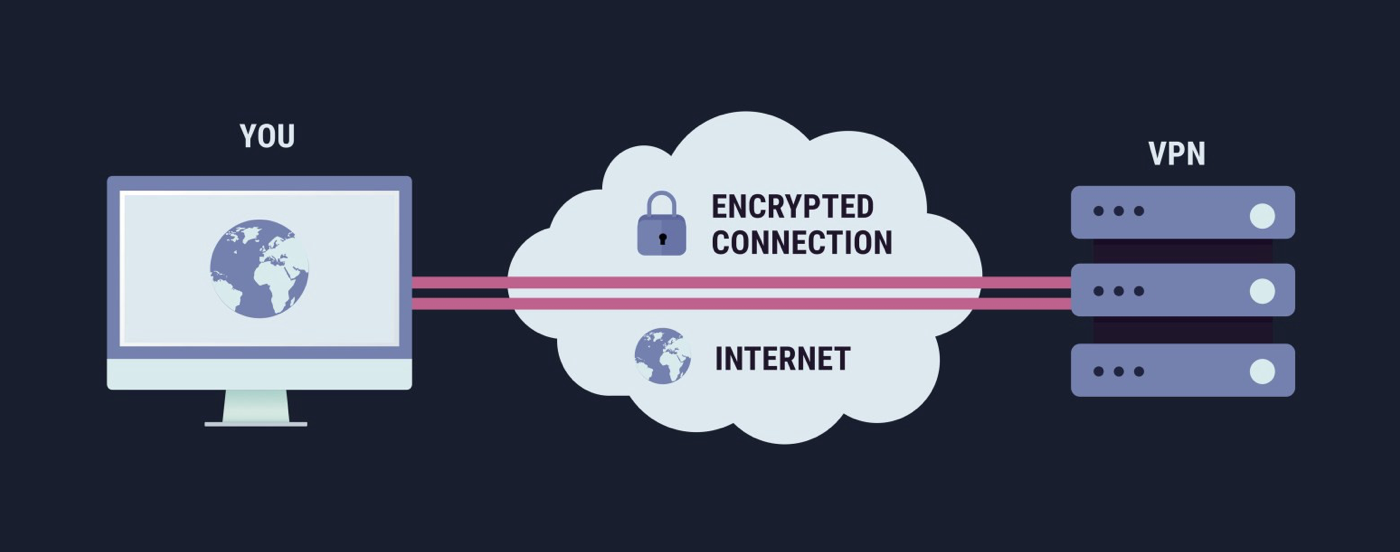
Navigating around internet censorship requires a blend of technological tools and a mindful approach to internet use. The goal is to access the full breadth of information and services available online while safeguarding personal privacy and security. Here’s how individuals can circumvent censorship using various methods:
VPNs (Virtual Private Networks)
VPNs create a secure and encrypted tunnel between a user's device and the internet, masking the user's IP address and rerouting their internet traffic through servers located in different countries. This process not only helps to bypass geographical restrictions and censorship but also enhances online privacy. By using a VPN, individuals can access content and websites that are blocked in their country, all while maintaining a level of anonymity. It’s essential to choose a reputable VPN provider to ensure strong encryption and no logging of user activity.
Proxy servers
Similar to VPNs, proxy servers act as intermediaries between the user's device and the internet. However, while proxies can change the apparent location and IP address, they may not offer the same level of encryption and security as VPNs. Proxies are useful for bypassing simple content restrictions by masking the user’s location. They're particularly handy for accessing region-locked content or websites blocked by local networks.
Secure browsers
Browsers designed with privacy and security in mind, such as Tor (The Onion Router), route internet traffic through multiple layers of encryption and across several nodes worldwide. This process anonymizes the user’s location and usage. Secure browsers allow users to access the web anonymously, making it difficult for authorities or ISPs to track their browsing activity. While they offer a high degree of privacy, they might not be as fast as conventional browsers due to their layered encryption.
Private DNS servers
DNS servers translate domain names into IP addresses. By default, your internet traffic goes through your ISP’s DNS servers, possibly subjecting you to censorship and monitoring. Switching to a private or alternative DNS service can bypass censorship filters implemented through DNS manipulation.
Each of these tools offers a pathway to circumvent internet censorship, but it's important for users to remain aware of the legal and ethical considerations in their jurisdiction.
Global examples of internet censorship
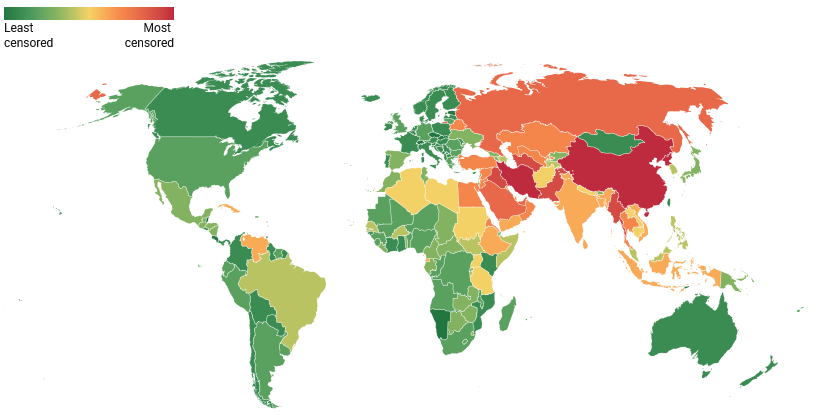
Internet censorship manifests in various forms around the globe, reflecting diverse political, cultural, and legal landscapes.
1. The Great Firewall of China
Perhaps the most extensive censorship system in the world, the Great Firewall is a combination of legislative actions and technologies enforced by the Chinese government to regulate the internet domestically. It blocks access to many foreign websites, including Google, Facebook, Twitter, and YouTube, and heavily monitors and censors internet traffic within the country. The censorship limits the flow of information, suppresses dissent, and controls how the Chinese public interacts with the global internet.
2. Iran's National Internet
Iran has implemented a national information network that controls and filters the content accessible to its citizens, blocking a wide range of foreign websites and services, especially those that offer unfiltered news or support free speech.
3. Russia's Internet Sovereignty Law
Enacted to give the government more control over the internet within Russia, this law includes measures to create an independent internet infrastructure that can operate separately from the global internet, allowing the government to increase its censorship capabilities.
4. Turkey's Social Media Regulations
Turkey has implemented strict regulations on social media platforms, requiring them to comply with local censorship laws. This includes removing content deemed offensive or a threat to national security and providing user data upon government request.
5. India's Internet Shutdowns
India has frequently used internet shutdowns as a tool for controlling unrest and limiting public organization, particularly in regions experiencing political tensions, such as Jammu and Kashmir.
6. North Korea's Restricted Internet
In North Korea, the internet is heavily restricted, with access to the global internet limited to a small number of government officials. The majority of the population can only access a government-controlled intranet, known as Kwangmyong, which offers a curated selection of content.
Conclusion
In the ever-evolving tapestry of the digital world, internet censorship stands as a significant force, shaping the contours of online discourse, access to information, and the freedom of expression. The mechanisms and motivations behind censorship are as varied as the global landscape itself, reflecting a complex interplay between the desire for security, the maintenance of social order, and the fundamental human rights to privacy and free speech.




Comments 0