
In the complex and multifaceted realm of digital privacy and online security, selecting the right operating system is crucial, especially for those venturing into the enigmatic depths of the dark web. This comprehensive guide delves into the intricacies of three leading privacy-focused operating systems: Tails OS, Whonix, and Qubes OS. Each system offers unique capabilities and security mechanisms tailored to safeguard your online identity and activities on the dark web. Let’s explore which of these might be the best fit for your specific needs.
- Exploring the Dark Web
- Tails OS
- Whonix
- Qubes OS
- Conclusion: Which is best for Dark Web activities?
- FAQs
Exploring the Dark Web
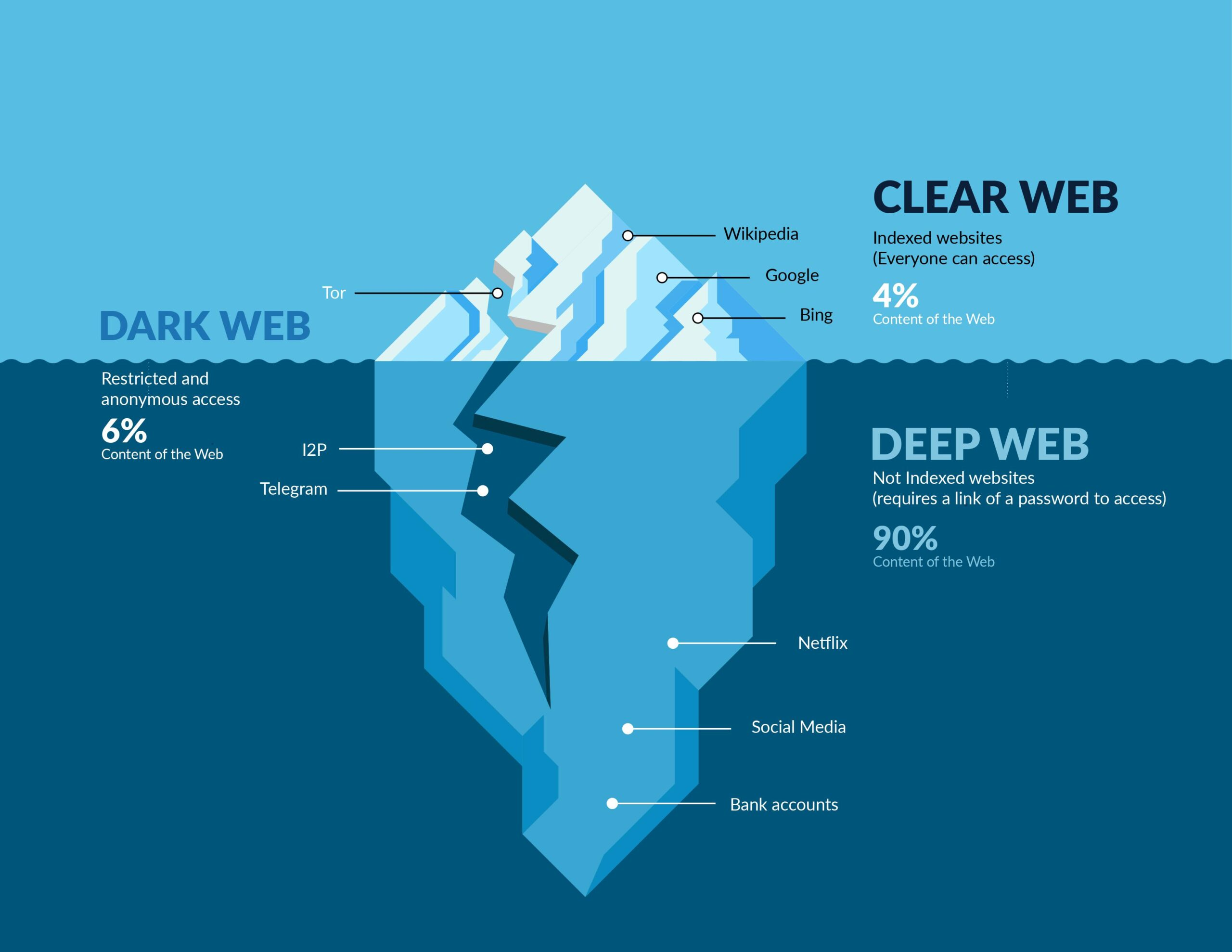
The term "Dark Web" often conjures images of a hidden underworld teeming with illicit activities, but the reality is more nuanced. The Dark Web refers to parts of the internet that are not indexed by standard search engines like Google or Bing and cannot be accessed through regular web browsers. To access the Dark Web, users must employ special software that anonymizes their online presence, the most common being the Tor browser.
The Dark Web is a small segment of the Deep Web, which includes all parts of the internet that are not indexed by search engines. This includes anything behind a paywall, such as certain parts of academic journals, private databases, and other subscription-based services, as well as the Dark Web. The Dark Web itself is encrypted and hidden, designed explicitly for anonymity. This design ensures that both the providers and users of the content can remain anonymous or untraceable.
The Dark Web serves various purposes. It is often portrayed as a haven for criminal activities, and while it does host illegal marketplaces for drugs, counterfeit currency, and even worse crimes, this is not its sole use. It also serves as a refuge for whistleblowers, activists, and journalists to communicate securely, especially within oppressive regimes where communication is heavily monitored or restricted.
The Dark Web is frequently misunderstood. The most common misconceptions include:
- It's entirely illegal. While illegal activities can take place, the Dark Web itself is not illegal. It's a tool, much like the internet at large, and can be used for both good and ill.
- It's only for tech-savvy individuals. Accessing the Dark Web is becoming increasingly user-friendly with tools and guides making it accessible to non-technical users.
- It’s large. Relative to the surface web, the Dark Web is quite small. The vast majority of internet use takes place on the visible internet, accessible through standard browsers and search engines.
Tails OS
Tails OS, short for The Amnesic Incognito Live System, stands as a beacon of privacy in the digital world. Crafted for users who prioritize anonymity and security, this free and open-source operating system ensures that each session leaves no trace behind.
Overview of Tails OS
Launched in 2009, Tails OS was designed with one core principle in mind: preserving user privacy and anonymity. It operates as a live system, which means it can be booted from a USB stick or a DVD without requiring installation on a computer's hard drive. This feature makes Tails OS particularly valuable for users who need to operate on different computers without leaving traces.
Core features of Tails OS
- Amnesic system. Perhaps the most defining characteristic of Tails OS is its amnesic nature. Once you shut down Tails, the operating system erases any trace of user activity from the hardware, unless explicitly saved in the encrypted persistent storage.
- Tor integration. All network traffic on Tails is routed through the Tor network, obscuring users' location and browsing habits from potential snoops and trackers. Tor also helps circumvent censorship, allowing access to the web's deeper layers and blocked sites.
- Pre-installed security tools. Tails comes equipped with a suite of security tools. These include encrypted email software, instant messaging clients with Off-the-Record (OTR) encryption, and the KeePassXC password manager to securely store and manage credentials.
- Persistent storage. While Tails does not keep any data after shutdown, it offers an option to create an encrypted persistent volume on the USB stick. This space can be used to store essential files, encryption keys, and configurations, which are restored on each boot.
Use cases for Tails OS
Tails OS is particularly suited for journalists, activists, and anyone else who needs to keep their digital communication private and secure. Its robust anonymity tools make it a favored choice for:
- Safeguarding sensitive communications from surveillance.
- Accessing the internet in highly censored regions.
- Conducting sensitive research without risking personal data exposure.
Strengths and limitations
Strengths:
- High portability. Tails can be used on almost any computer from a USB stick or DVD.
- Strong privacy protections. With all traffic routed through Tor and no data persistence, it offers strong privacy by design.
- Free and open source. Users can review the source code, contributing to transparency and trust.
Limitations:
- Hardware compatibility. Some users may encounter issues with hardware compatibility, particularly with very new or very old components.
- Performance. Routing traffic through Tor can slow down internet speeds, and running from a USB may not provide the fastest system response.
Whonix
Whonix is an open-source operating system designed for users who prioritize ultimate privacy and security. Renowned for its unique approach to anonymity, Whonix operates on the principle of isolation, using separate virtual machines to compartmentalize internet traffic and applications.
Overview of Whonix
Developed with a focus on user anonymity and security, Whonix leverages the power of virtualization technology to segregate the user's computing environment into two distinct parts: the Whonix-Gateway and the Whonix-Workstation. This structure is aimed at preventing malware from discovering the user's real IP address and other sensitive information.
Key features of Whonix
- Isolation through virtualization. The fundamental architecture of Whonix splits the operating system into two virtual machines. The Whonix-Gateway only runs Tor processes and acts as a Tor gateway, which means that all connections are forced through the Tor network. The Whonix-Workstation, on the other hand, is completely isolated from the network and can only connect through the gateway, ensuring that no real IP leaks are possible.
- Secure network architecture. By default, every application in Whonix is configured to connect to the internet through Tor, mitigating risks associated with DNS leaks and other forms of data interception.
- Compatibility and flexibility. Whonix can be run inside existing operating systems using virtual machine platforms like VirtualBox or QEMU. This makes it highly compatible and flexible, able to operate on Windows, macOS, and Linux without requiring specialized hardware.
- Pre-installed security tools. Whonix comes with a plethora of pre-configured and pre-installed security tools, including privacy-enhancing software and encryption tools. This ready-to-use suite helps users protect their digital information right from the start.
Use cases for Whonix
Whonix is particularly useful for:
- Users operating in environments with high surveillance and censorship.
- Professionals handling sensitive information who require an additional layer of security to prevent data breaches.
- Researchers and academics needing to access and share confidential data without exposing their identity or location.
Strengths and limitations
Strengths:
- Robust privacy protections. With all communications routed through Tor and strict network isolation, Whonix provides strong safeguards against tracking and surveillance.
- No direct internet access. The workstation’s inability to make direct internet connections virtually eliminates the risk of IP leaks, even if malware compromises the system.
- Open source transparency. Users can review and modify the source code, ensuring trust and the ability to independently verify security claims.
Limitations:
- Resource intensity. Running two virtual machines simultaneously can be resource-intensive, requiring a decently powerful computer to operate efficiently.
- Complex setup. The initial setup might be daunting for less technical users, given the complexity of configuring and maintaining two separate virtual environments.
Qubes OS
Qubes OS is distinguished in the realm of operating systems for its revolutionary approach to security by compartmentalization. Utilizing Xen-based virtualization technology, Qubes OS allows users to operate multiple virtual machines as isolated compartments, thereby significantly reducing the risk of system-wide breaches.
Overview of Qubes OS
Introduced with the aim of providing superior security through isolation, Qubes OS adopts a unique architecture where applications run within separate virtual machines, known as qubes. This design philosophy ensures that activities carried out in one qube cannot affect another, making Qubes an ideal platform for managing diverse tasks with varying security needs—from browsing the internet to handling sensitive data.
Key features of Qubes OS
- Security through isolation. The cornerstone of Qubes OS is its ability to keep different application environments strictly separated. For example, a VM for browsing untrusted websites is kept completely independent from a VM handling confidential documents.
- Integrated networking. Network connections are handled by a dedicated, isolated virtual machine, preventing any direct access to the main operating system or other sensitive virtual machines.
- Customizable security levels. Qubes OS allows users to define the security level of virtual machines using color-coded trust levels. This visual cue helps users easily manage and distinguish between trusted and untrusted applications or environments.
- Template system. Virtual machines in Qubes are based on templates, which means that multiple VMs can use the same root file system without compromising isolation. This not only enhances security but also optimizes system resources.
Use cases for Qubes OS
Qubes OS is particularly suited for:
- Security professionals and organizations that handle highly sensitive information and require robust compartmentalization.
- Individuals seeking to protect their personal data from cyber threats, especially those who regularly handle sensitive financial or personal information.
- Researchers and developers who need to test software in secure, isolated environments to prevent potential system contamination.
Strengths and limitations
Strengths:
- Comprehensive isolation. Each virtual machine operates independently with its own set of resources, offering unparalleled security by design.
- Versatility and flexibility. Users can run applications from different operating systems, like Fedora, Debian, and even Windows, in separate qubes.
- User control and customization. Offers extensive customization options for tailoring security settings to specific needs.
Limitations:
- Hardware demands. Qubes OS requires a computer with adequate RAM and CPU capabilities, as running multiple VMs is resource-intensive.
- Steep learning curve. The complexity of managing various isolated VMs and understanding the Qubes model can be challenging for new users.
- Compatibility issues. Some hardware may not be compatible with the virtualization technology used by Qubes, potentially requiring adjustments or specific configurations.
Conclusion: Which is best for Dark Web activities?
When choosing the best operating system for navigating the dark web, the decision hinges on your specific requirements, including your need for security, versatility, and the type of hardware you use.
- Whonix is ideal for users who prioritize a high level of security and are comfortable with setting up and maintaining virtual machines. Its use of isolated VMs for internet gateway and workstation functions provides strong protection against network attacks and ensures that any potential compromise does not affect the entire system. Whonix is especially suited for individuals who perform their dark web activities from a fixed location and need a consistent, secure environment for daily use.
- Tails OS excels in situations where users need to access the internet securely and anonymously on different computers. As it runs directly from a USB stick and leaves no trace on the host machine, Tails OS is perfect for conducting sensitive operations on public or shared computers. The system's portability and ease of use, combined with its robust set of pre-installed security tools, make it ideal for tasks like online banking or handling confidential information in various locations.
- Qubes OS offers the highest level of security through its advanced compartmentalization approach, where each application operates within its own virtual machine. This architecture not only prevents security breaches in one VM from affecting others but also allows for a highly customizable security setup, where the sensitivity of data dictates the security level of the VM. Qubes OS is recommended for technically savvy users who require stringent security measures and can manage multiple, segregated environments effectively.
FAQs
Why do I need a special operating system to access the darknet?
Specialized operating systems like Tails OS, Whonix, and Qubes OS provide enhanced security features and anonymity tools that are essential for safely navigating the dark web, protecting users from potential threats and ensuring privacy.
Do I need technical expertise to use these operating systems?
Tails OS is user-friendly and requires minimal setup, making it accessible even to those with limited technical expertise. Whonix and Qubes OS, however, involve more complex setups with VMs and may require a higher level of technical knowledge to use effectively.




Comments 0